What Is SSH Command – Usage, Configuration
Introduction
Have you ever wondered how system administrators securely manage remote servers from across the globe? The answer lies in the SSH command—a powerful tool that transforms how we interact with distant systems. Whether you’re executing vital tasks or safeguarding sensitive data, SSH provides an encrypted pathway that ensures your connection is both secure and efficient. It’s more than just a protocol; it’s the backbone of modern server management. Discover how mastering the usage, options, and configuration of the SSH command can enhance your control over remote systems like never before. Ready to unlock its potential?
Table of Contents
What is SSH Protocol
The SSH (Secure Shell) protocol is a cryptographic network protocol designed to secure communication between two systems, typically a client and a server. It provides a secure method for users to log into remote machines and execute commands or transfer files, all while encrypting the data in transit to prevent unauthorized access. SSH replaces less secure protocols like Telnet and rlogin, ensuring that sensitive information, such as passwords and configuration details, remains protected from interception. Widely used in network administration, SSH supports strong encryption, authentication, and secure tunneling, making it a cornerstone of modern cybersecurity practices.
Connect to Linux Server via SSH
Connecting to a Linux server via SSH is a fundamental task in system administration, allowing secure access to remote machines over an encrypted network. The process is simple but powerful, enabling users to manage files, run commands, and configure systems from any location.
Step-by-Step Description:
1- Open a Terminal: Whether you’re using macOS, Linux, or even Windows (via tools like PuTTY or Windows Terminal), the first step is to launch your terminal or command prompt.
2- SSH Command Format: The core of the connection process lies in the SSH command:

- username: The account you’re logging into on the remote machine.
- server_ip_address: The IP address or domain of the Linux server you’re trying to access.

This tells your machine to initiate a secure connection to the remote server at 192.168.1.1, logging in with the username admin.
3- Port Specification (Optional): By default, SSH connects on port 22, but if your server uses a different port for added security, you’ll need to specify it:
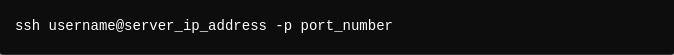
Example:

4- Authentication: Upon running the command, you’ll be prompted for the password of the remote user. Once entered, SSH creates a secure, encrypted session. For an extra layer of security, many administrators prefer key-based authentication.
5- Key-based Authentication: Instead of entering a password, you can use SSH keys (a public and private key pair) to authenticate. If you’ve set up SSH keys, the server will automatically verify your identity using the private key stored on your local machine, bypassing the need for a password:
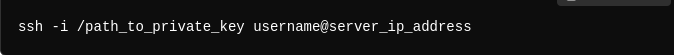
6- Secure File Transfer with SSH: SSH also supports secure file transfers using SCP or SFTP. For example, to copy a file from your local machine to the server:
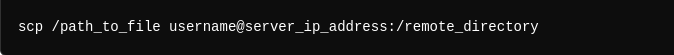
Once connected, you have full access to the server’s command-line interface, enabling you to manage the system remotely with unparalleled security and flexibility.
SSH Command in Linux
The SSH command in Linux is a powerful tool used to securely access and manage remote systems. It allows users to initiate encrypted connections between a client and a server over an unsecured network, ensuring data integrity and privacy. With SSH, system administrators can log in to a remote server, execute commands, transfer files, and manage configurations seamlessly.
Basic SSH Command Format:

username: The username you’re logging in as on the remote machine. remote_host: The IP address or domain name of the remote server.
Common Usage Options:
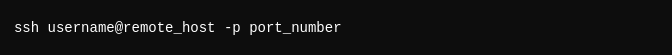
Specify Port: SSH by default uses port 22. To connect via a different port:
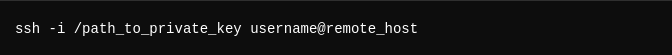
Connect Using SSH Keys: For key-based authentication (without needing a password):
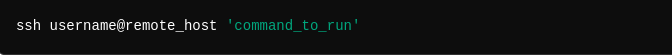
Execute a Command on a Remote Server: You can run a specific command remotely and get the output locally:
Key SSH Options:
-l: Specify a different username:

-v: Enable verbose mode to help debug connection issues:

-X: Enable X11 forwarding to run graphical applications remotely:

Configuration:
You can simplify your SSH connections by configuring them in the ~/.ssh/config file. For instance:

This allows you to connect to myserver with just:

The SSH command is an indispensable tool for secure, remote system management in Linux environments, offering flexibility through its various options and configurations.
In the realm of cybersecurity, the ssh command stands as a vital safeguard, ensuring that every remote connection is encrypted and secure.
Using the Linux Client
Using the Linux client for SSH is straightforward and highly efficient for managing remote systems securely. The SSH client is built into most Linux distributions, enabling quick access to remote servers without the need for additional software.
Steps to Use the Linux SSH Client:
1- Open the Terminal: The terminal is your gateway to executing the SSH command in Linux. Simply launch the terminal on your machine, which is available in all major Linux distributions.
2- SSH Command Structure: The basic syntax for connecting to a remote server is:

- Replace
usernamewith the username of the account on the remote server. - Replace
server_ip_addresswith the actual IP address or domain of the remote machine.
3- Authentication: Once the SSH command is entered, you’ll be prompted to provide the password for the user account on the server. Upon successful authentication, you’ll gain access to the server’s command-line interface.
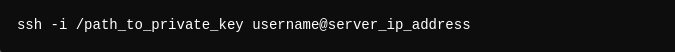
4- Key-based Authentication: If SSH keys have been set up, you can connect using your private key. This eliminates the need to enter a password:
5- Using SSH Config File: Linux allows you to simplify SSH connections using the SSH config file, typically located in ~/.ssh/config. Here’s an example:

Now, to connect to myserver, simply run:

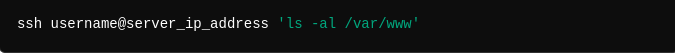
6- Run Remote Commands: You can run commands directly on the remote server without logging into an interactive session. For example:
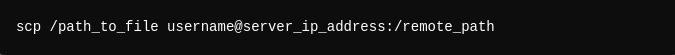
7- Secure File Transfers: The SSH client also enables secure file transfers using SCP (Secure Copy Protocol) or SFTP (Secure File Transfer Protocol). For instance, to copy a file from your local machine to the server:
Additional SSH Client Options:
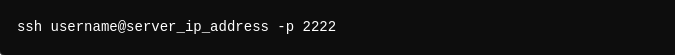
-p: Specify a non-default port.
-L: Set up local port forwarding.
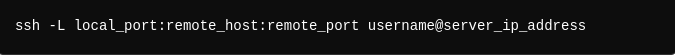
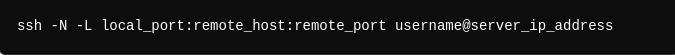
-N: Don’t execute remote commands, just forward ports.
SSH Client Configuration File
The SSH command is more than just a tool for remote access; it becomes a powerhouse when you leverage the SSH client configuration file. Stored in ~/.ssh/config, this file simplifies managing multiple SSH connections by defining custom settings for each server. No longer will you need to remember intricate commands or multiple IP addresses. Instead, a streamlined configuration file lets you define aliases, ports, usernames, and even the identity files needed for specific connections.
For example, instead of typing the full ssh command each time, you can configure:

With this in place, a simple ssh myserver handles the rest. This file brings simplicity to complexity, allowing seamless server management, automating key-based authentication, and optimizing secure access. The SSH client configuration file is an elegant solution for those managing multiple systems, empowering users to efficiently navigate the world of remote servers with minimal effort while using the ssh command.
The ssh command is not just a tool; it’s a gateway to secure and efficient remote management in a digital landscape.
Conclusion
In conclusion, the ssh command stands as a cornerstone of secure remote management, empowering users to access and control systems with precision and confidence. Whether you’re navigating a network of servers or simply managing a single machine, the versatility of this tool cannot be overstated. Its ability to encrypt data, streamline connections, and facilitate seamless command execution makes it indispensable for both seasoned administrators and new users alike. The ssh command embodies the essence of security and efficiency, offering a gateway to simplified, yet powerful, remote operations in an increasingly interconnected world.
Mastering the ssh command empowers system administrators to navigate complex networks with confidence and security.
FAQ: SSH Command
1. What is the SSH command?
The ssh command is a tool used to securely access and manage remote systems. It establishes encrypted connections between a client and server, allowing users to execute commands, transfer files, and control remote machines.
2. How does the SSH command ensure security?
The ssh command uses strong encryption protocols to secure communication between the client and server, protecting data from interception and unauthorized access.
3. Can I use the SSH command to transfer files?
Yes, the ssh command supports secure file transfer protocols like SCP and SFTP, allowing you to securely transfer files between your local machine and a remote server.
4. What are SSH keys, and how do they work with the SSH command?
SSH keys are cryptographic pairs used to authenticate users without a password. You can use them with the ssh command by generating a key pair and storing the public key on the remote server for passwordless access.





online canadian discount pharmacy
canadapharmacy com
canadian pharmacieswith no prescription
online canadian pharmacy
canadian world pharmacy
discount pharmacies online
sildenafil tablets
best viagra prices
canadian pharmacies online reviews
canadian online pharmacies not requiring a prescription
sildenafil viagra
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
most trusted online pharmacy