How DDoS Mitigation Works

What would you do if your online business was suddenly unreachable, drowning in a flood of malicious traffic? In an era dominated by digital dependence, the threat of a DDoS attack looms large, capable of crippling websites, tarnishing reputations, and draining revenue in an instant. Imagine your servers drowning under an ocean of malicious traffic, locking out legitimate users at the worst possible moment. This is where DDoS mitigation becomes indispensable a meticulously engineered safeguard that detects, deflects, and dismantles these digital sieges. Beyond protection, it ensures continuity, shields user trust, and fortifies your online presence. Understanding DDoS mitigation is not just a necessity; it’s your weapon against the chaos of modern cyber warfare.
Table of Contents
What Is DDoS Attack?
A DDoS (Distributed Denial of Service) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming it with a flood of internet traffic. Unlike a traditional Denial of Service (DoS) attack, which originates from a single source, a DDoS attack leverages multiple compromised systems—often distributed across the globe—making it more challenging to mitigate.
How a DDoS Attack Works ?
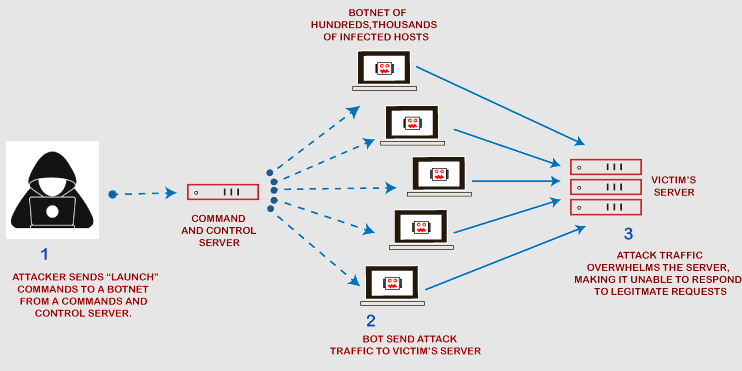
1. Building the Attack Network
Attackers prepare for the attack by creating a network of compromised devices, known as a botnet.
- Infection Process: Devices (like computers, IoT devices, or smartphones) are infected with malware, often through phishing emails, malicious downloads, or exploiting software vulnerabilities.
- Botnet Control: The infected devices act as “zombies,” controlled remotely by the attacker through a Command-and-Control (C&C) server.
2. Target Selection
The attacker identifies a target, which could be:
- A popular website (e.g., e-commerce platforms or news sites).
- Online services (e.g., gaming servers or financial systems).
- Specific IP addresses or networks.
3. Traffic Generation
Once the botnet is ready, the attacker instructs all infected devices to send massive amounts of traffic to the target simultaneously. This traffic can take several forms:
- Requests: Simulating legitimate user activity, such as accessing a webpage or requesting resources.
- Data Packets: Sending large volumes of data to exhaust bandwidth.
- Connection Attempts: Overloading network protocols like TCP, UDP, or HTTP.
4. Overloading the Target
The excessive volume of incoming traffic overwhelms the target’s resources:
- Bandwidth Saturation: The internet connection capacity is exceeded, causing network congestion.
- CPU/Memory Exhaustion: Servers become unable to process legitimate requests due to resource depletion.
- Service Breakdown: Applications or websites slow down or crash, leading to unavailability for legitimate users.
5. Sustaining the Attack
The attack continues for as long as the botnet remains active, causing prolonged disruption. Some attacks escalate by:
- Randomizing traffic patterns to avoid detection.
- Switching between different types of attacks to confuse defenses.
Types of DDoS Attacks ?
1. Volumetric Attacks
These attacks aim to flood the target’s network with excessive traffic, overwhelming bandwidth and causing legitimate requests to be blocked.
Examples:
- UDP Floods: Send a massive number of User Datagram Protocol (UDP) packets to random ports, forcing the target to check for nonexistent applications.
- ICMP Floods (Ping Flood): Overwhelm the target with ICMP echo requests (pings), saturating the network.
- Amplification Attacks: Use open servers (e.g., DNS or NTP) to amplify the amount of traffic sent to the victim.
- DNS Amplification: Leverages small queries to trigger large responses sent to the target.
2. Protocol Attacks
Also called state-exhaustion attacks, these exploit weaknesses in network protocols to overwhelm server resources like memory or connection tables.
Examples:
- SYN Floods: Exploit the TCP handshake by sending a flood of SYN requests but never completing the connection, exhausting server resources.
- Ping of Death: Sends oversized or malformed packets that can crash or destabilize the target system.
- Smurf Attack: Sends ICMP requests with a spoofed source address (the target), causing multiple devices to flood the target with replies.
3. Application Layer Attacks
These target specific applications (e.g., HTTP, DNS, or VoIP) by mimicking legitimate user behavior, making them harder to detect.
Examples:
- HTTP Floods: Overload web servers by sending numerous GET or POST requests.
- Slowloris: Keeps many connections to the server open but sends data very slowly, exhausting server connections.
- DNS Query Flood: Overloads DNS servers with numerous queries, affecting domain resolution.
4. Fragmentation Attacks
These involve sending fragmented packets that the target must reassemble, consuming computational resources.
Examples:
- IP Fragmentation Attacks (Teardrop Attack): Send fragmented IP packets that cannot be properly reassembled, causing systems to crash.
- UDP Fragmentation: Overwhelms resources by sending fragmented UDP packets.
5. Advanced Persistent DoS (APDoS)
A sophisticated and sustained attack combining multiple techniques, including volumetric, protocol, and application-layer attacks, for prolonged disruption.
Features:
- High intensity and duration.
- Frequent use of evasion techniques, like spoofed IPs.
6. IoT-Based DDoS Attacks
These leverage the growing number of Internet of Things (IoT) devices, which are often poorly secured.
Example:
- Mirai Botnet Attack: Infected IoT devices to generate massive traffic, disrupting large-scale services like DNS providers.
Comparison Table:
| Type | Target | Method | Example | Impact |
| Volumetric | Bandwidth | Floods of data | UDP Flood, DNS Amplification | Bandwidth exhaustion |
| Protocol | Network infrastructure | Exploits protocol vulnerabilities | SYN Flood, Ping of Death | Resource depletion |
| Application Layer | Specific applications | Mimics legitimate user behavior | HTTP Flood, Slowloris | Server performance impact |
| Fragmentation | Systems handling packets | Sends fragmented packets | Teardrop, UDP Fragmentation | System crashes |
| IoT-Based | IoT networks | Botnets of compromised IoT devices | Mirai | Large-scale disruption |
What Is DDoS Mitigation?
DDoS mitigation is the process of protecting networks, servers, and online services from the debilitating effects of a Distributed Denial of Service (DDoS) attack. This involves identifying and neutralizing malicious traffic before it overwhelms the target system, ensuring uninterrupted service availability. By employing sophisticated detection systems, DDoS mitigation differentiates legitimate user requests from the deluge of malicious data, preserving bandwidth and computing resources.
Modern DDoS mitigation strategies often rely on layered defenses, including traffic filtering, rate limiting, and leveraging global Content Delivery Networks (CDNs). These measures work in tandem to absorb or redirect excessive traffic, safeguarding critical infrastructure. Advanced systems utilize behavioral analysis and artificial intelligence to swiftly adapt to evolving attack patterns. In a landscape where cyber threats grow increasingly complex, DDoS mitigation stands as a critical safeguard, fortifying businesses against financial losses, reputational harm, and operational disruptions.
Effective DDoS mitigation isn’t just about blocking attacks; it’s about ensuring uninterrupted access for legitimate users.
Best Practices for DDoS Protection
Effective protection against Distributed Denial of Service (DDoS) attacks requires a proactive and multi-layered approach. Implementing the following best practices helps mitigate threats while ensuring service continuity:
- Deploy Scalable Infrastructure
- Invest in cloud-based solutions that offer elasticity to handle surges in traffic. Leveraging global load balancers and Content Delivery Networks (CDNs) helps disperse traffic and reduce the risk of overload.
- Implement DDoS Mitigation Tools
- Use advanced DDoS mitigation services that analyze traffic in real-time and block malicious requests. These tools often incorporate machine learning and behavior analysis to adapt to evolving attack patterns.
- Use Rate Limiting and IP Whitelisting
- Limit the number of requests allowed per user in a given timeframe. IP whitelisting ensures only trusted sources can access critical applications.
- Monitor Network Traffic Continuously
- Anomalies such as sudden spikes or unusual patterns can indicate an attack. Employ intrusion detection systems (IDS) and automated alerts for swift responses.
- Regularly Update Security Protocols
- Keep firewalls, routers, and software patches current to close vulnerabilities that attackers might exploit. Combine this with penetration testing to identify weak points.
Create a DDoS Mitigation Plan
- Assess Network Vulnerabilities
- Identify critical systems, potential weak points, and bandwidth limitations to prioritize areas requiring protection.
- Implement DDoS Mitigation Tools
- Deploy advanced traffic filtering solutions capable of distinguishing malicious activity from legitimate users in real-time.
- Leverage Scalable Infrastructure
- Use cloud-based platforms and Content Delivery Networks (CDNs) to distribute traffic loads and absorb volumetric attacks effectively.
- Develop an Incident Response Plan
- Outline clear procedures for detecting, analyzing, and responding to DDoS attacks. Assign roles to ensure rapid execution.
- Conduct Regular Testing
- Simulate DDoS attacks to evaluate your mitigation strategies and identify potential gaps or inefficiencies.
- Monitor Traffic Continuously
- Use automated tools to track network behavior for anomalies that might indicate an incoming attack.
- Update Security Protocols Regularly
- Patch systems, update firewalls, and refine your DDoS mitigation strategies to stay ahead of evolving threats.
Four Stages of DDoS Mitigation
1. Detection
Detection is the cornerstone of any effective DDoS mitigation strategy. Early identification of unusual traffic patterns, such as sudden surges or repetitive requests from specific sources, enables swift response to potential threats. Advanced detection systems leverage behavioral analytics and anomaly detection algorithms to distinguish between legitimate user activity and malicious traffic.
Real-time monitoring tools are crucial, offering immediate alerts when anomalies occur. These systems analyze packet headers, traffic flow, and request frequency to flag potential attacks. By integrating automated tools with network infrastructure, businesses can neutralize threats before they escalate. Effective detection not only minimizes downtime but also forms the foundation for proactive DDoS mitigation, ensuring robust protection against evolving cyber threats.
2. Response
A swift and coordinated response is essential in DDoS mitigation to minimize damage during an attack. Once a potential threat is detected, predefined procedures should be activated to mitigate the impact. This involves redirecting traffic, filtering malicious requests, and implementing rate limiting to prevent network overload.
Communication with stakeholders is also crucial during this phase to ensure transparency. Leveraging DDoS mitigation tools can automate many of these actions, allowing for real-time adjustments as the attack evolves. Additionally, activating backup systems or cloud-based resources can help maintain service availability. The effectiveness of the response is often determined by how quickly and accurately these steps are executed, underscoring the importance of thorough preparation and rapid reaction in defending against DDoS threats.
3. Filtering
Filtering plays a critical role in DDoS mitigation, allowing systems to distinguish between legitimate traffic and malicious requests. By analyzing incoming data, filtering solutions can block harmful packets while allowing normal traffic to pass through unhindered. This process involves scrutinizing packet headers, identifying known attack signatures, and assessing traffic behavior for anomalies.
Advanced filtering techniques, such as rate limiting and IP blacklisting, can be employed to slow down or block attackers. Additionally, traffic can be routed through scrubbing centers, where DDoS mitigation tools clean the data before it reaches the target. Effective filtering minimizes the impact of the attack, ensuring that only valid users can access critical services while malicious traffic is kept at bay.
4. Analysis
In the context of DDoS mitigation, analysis is the process of thoroughly examining traffic patterns to identify malicious activities. By utilizing advanced monitoring tools, security teams can scrutinize the nature of incoming traffic, looking for signs of a potential attack. This analysis involves evaluating packet characteristics, source addresses, and request behaviors to differentiate between legitimate users and harmful traffic.
Effective analysis can help uncover attack vectors and predict the duration and intensity of the threat. By leveraging real-time data, teams can implement targeted countermeasures to block or limit malicious traffic. In DDoS mitigation, robust analysis is not just about identifying attacks but also about understanding evolving tactics, ensuring a more adaptive and resilient defense strategy.
In the digital age, robust DDoS mitigation strategies are the cornerstone of resilient cybersecurity.
Conclusion
In conclusion, DDoS mitigation is an essential strategy for safeguarding digital infrastructure against the increasing threat of cyberattacks. By implementing a combination of detection, filtering, and response mechanisms, organizations can reduce the impact of a DDoS attack. Early identification, coupled with swift countermeasures, ensures minimal disruption to services. As DDoS tactics evolve, continuous refinement of DDoS mitigation strategies becomes vital. Investing in robust defenses not only protects critical assets but also ensures business continuity, allowing organizations to maintain trust and operational stability in an increasingly hostile cyber landscape.
Proactive DDoS mitigation safeguards not only infrastructure but also the trust and reputation of your organization.
Frequently Asked Questions About DDoS Mitigation
- What is DDoS mitigation, and why is it important?
- DDoS mitigation refers to the process of detecting, analyzing, and preventing Distributed Denial of Service (DDoS) attacks. It is crucial for ensuring uninterrupted access to online services and protecting critical infrastructure from disruptions.
- How does DDoS mitigation work?
- DDoS mitigation involves monitoring traffic, identifying malicious patterns, and filtering out harmful data while allowing legitimate requests to pass through. It often employs tools like firewalls, rate limiters, and scrubbing centers.
- Can DDoS mitigation stop all types of attacks?
- While no solution guarantees complete protection, advanced DDoS mitigation techniques can address most known attack vectors and reduce the impact of even the most sophisticated attacks.
- What tools are commonly used for DDoS mitigation?
- Common tools include intrusion detection systems (IDS), Content Delivery Networks (CDNs), traffic monitoring software, and cloud-based DDoS mitigation services.
- Is DDoS mitigation expensive?
- The cost of DDoS mitigation varies based on the complexity of the solution. While basic protections are affordable, advanced services tailored to large-scale enterprises may require higher investment.





Incredible journey! Dinosaur Game has become a digital sanctuary in our fast-paced world.
From sketches to bangers: Sprunk accelerates music production!