What is a Firewall: Definition And Types

Is your network truly secure? In a world where cyber threats evolve daily, understanding the firewall is essential. This crucial barrier defends against malicious intrusions, safeguarding your data and ensuring peace of mind. Dive into the history, types, and critical functions of firewalls to arm yourself with the knowledge needed to protect your digital assets. Learn how modern firewall technologies go beyond simple packet filtering to provide robust, multi-layered security. Don’t leave your network vulnerable—explore the indispensable role of firewall systems in today’s cybersecurity landscape. Your digital defense starts here.
Table of Contents
What is a Firewall?

A firewall is a critical component in network security, acting as a barrier between a trusted internal network and untrusted external networks. It monitors and controls incoming and outgoing network traffic based on predetermined security rules. By analyzing data packets, a firewall can prevent unauthorized access and protect sensitive information. It operates at various layers of the OSI model, from packet filtering at the network layer to deep packet inspection at the application layer. In essence, a firewall serves as the first line of defense against cyber threats, ensuring the integrity and security of your network infrastructure.
History of Firewalls
The firewall has evolved significantly since its inception in the late 1980s. Initially, simple packet filters were designed to control traffic based on IP addresses, protocols, and ports. These first-generation firewalls provided basic security but lacked the sophistication needed to handle more complex threats.
In the 1990s, the introduction of stateful inspection marked a major advancement. These second-generation firewalls could track the state of active connections and make more informed decisions about which packets to allow through.
The early 2000s saw the advent of application-layer firewalls, or proxy servers, which could inspect traffic at the application level, providing a more granular level of security.
Today, Next-Generation Firewalls (NGFW) incorporate advanced features like deep packet inspection, intrusion prevention systems, and application awareness. These modern firewall technologies offer comprehensive protection against a wide array of cyber threats, making them indispensable in contemporary network security.
The Different Types of Firewalls
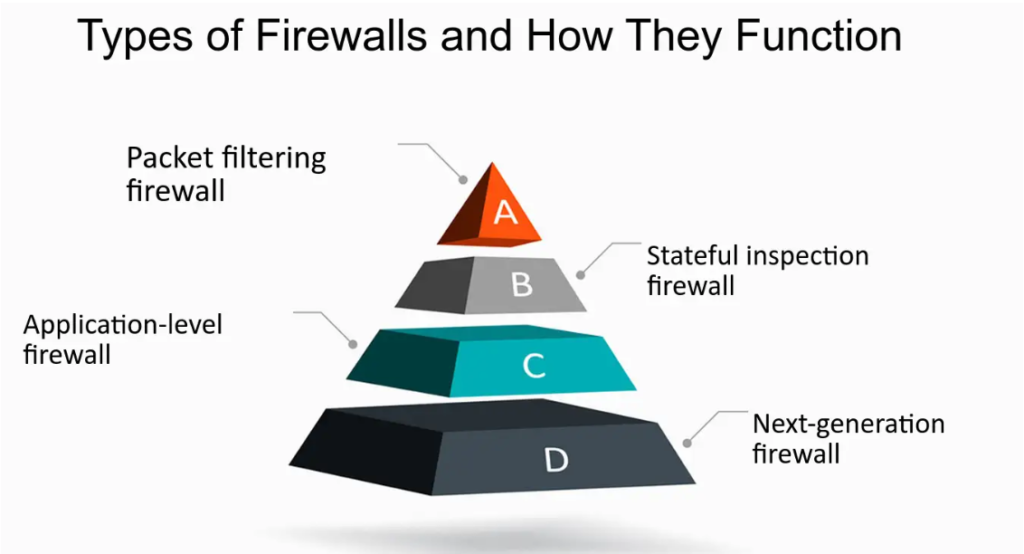
Packet Filtering
Packet filtering is a fundamental firewall technique that controls network access by analyzing incoming and outgoing packets. It inspects each packet’s header to determine its source and destination IP addresses, protocol, and port number. Based on predefined security rules, the firewall decides whether to allow or block the packet. This method is efficient and fast, providing a basic level of security by preventing unauthorized access. However, packet filtering firewalls lack the capability to inspect the payload of packets, making them less effective against more sophisticated attacks that operate at higher layers of the OSI model.
Proxy Service
A proxy service acts as an intermediary between a user’s device and the internet, providing an additional layer of security and privacy. When configured within a firewall, a proxy server filters requests and responses, ensuring that only legitimate traffic passes through. This setup helps conceal internal IP addresses, thereby safeguarding network anonymity. By examining data packets at the application level, proxy services can detect and block malicious content, enforce security policies, and manage bandwidth usage. Implementing a proxy service within a firewall enhances network defense mechanisms, offering robust protection against various cyber threats while optimizing network performance.
Stateful Inspection Firewall
A stateful inspection firewall is an advanced type of firewall that monitors the state of active connections and makes decisions based on the context of traffic. Unlike traditional packet filtering, it examines both the header and the state of the packet within the traffic flow. This allows it to keep track of the established connections and ensure that only legitimate packets are allowed through. By maintaining a state table, it can identify and block malicious traffic patterns that a simple packet filter might miss. This comprehensive approach enhances the security and effectiveness of the firewall in protecting networks from sophisticated attacks.
Next Generation Firewall (NGFW)
A Next Generation Firewall (NGFW) represents the evolution of traditional firewall technology, integrating advanced features to address modern cybersecurity challenges. Beyond simple packet filtering and stateful inspection, NGFWs incorporate capabilities such as deep packet inspection, intrusion prevention systems (IPS), and application awareness. They can identify and control applications regardless of port, protocol, or evasive tactics, providing granular visibility and control. By combining these advanced functionalities, NGFWs offer superior protection against sophisticated threats like malware and exploits. Deploying a Next Generation Firewall ensures comprehensive security, meeting the demands of contemporary network environments while enhancing overall defense strategies.
What Does A Firewall Do?
- Traffic Monitoring: A firewall continuously inspects all incoming and outgoing data packets. This constant vigilance helps in identifying any irregularities or anomalies that could indicate a security threat.
- Access Control: By enforcing rules that specify which traffic is permitted or denied, a firewall restricts access based on IP addresses, domain names, and port numbers. This selective access helps in preventing unauthorized users from breaching the network.
- Threat Prevention: Advanced firewalls employ deep packet inspection and intrusion prevention systems (IPS) to detect and block malicious threats such as viruses, worms, and exploit attempts. This proactive defense mechanism helps in mitigating risks before they can impact the network.
- Network Segmentation: A firewall can segment a network into distinct zones or segments, isolating sensitive data and critical systems from the rest of the network. This segmentation limits the potential spread of attacks and enhances security by containing potential breaches.
- Logging and Reporting: It maintains detailed logs of all network traffic, including successful and blocked connection attempts. This data is crucial for forensic analysis, monitoring network activity, and ensuring compliance with security policies and regulations.
- User Authentication: Some firewalls integrate with authentication systems to ensure that only verified and authorized users can access certain network resources. This added layer of security helps in preventing unauthorized access.
- VPN Support: Firewalls often support Virtual Private Networks (VPNs), enabling secure remote access to the network. By encrypting data transmitted over the internet, they ensure that remote users can connect safely and confidentially.
- Application Layer Filtering: Modern firewalls can inspect traffic at the application layer, allowing for more granular control over specific applications and services. This capability helps in blocking unwanted applications while allowing legitimate ones to function.
- Bandwidth Management: Some firewalls offer features to prioritize network traffic, ensuring that critical applications receive the necessary bandwidth and reducing the impact of non-essential traffic on network performance.
- Policy Enforcement: Firewalls enforce security policies by applying rules consistently across the network. This ensures that security measures are uniformly implemented, reducing the risk of misconfigurations and vulnerabilities.
Why Do We Need Firewalls?
- Threat Mitigation: Firewalls are designed to filter and scrutinize incoming and outgoing traffic based on predefined security rules. By doing so, they block or allow data packets, preventing malware, viruses, and unauthorized access attempts from penetrating the network. This proactive approach ensures that malicious entities are intercepted before causing damage.
- Access Control: Firewalls enforce access policies to determine which users or systems can access specific resources. This is crucial in preventing unauthorized access and safeguarding sensitive information. Through rule-based configurations, firewalls restrict access to critical systems and data, thus reducing the risk of data breaches.
- Network Segmentation: Firewalls facilitate network segmentation by dividing the network into distinct zones. This segmentation limits the impact of security incidents by isolating them within specific segments. If a breach occurs in one segment, firewalls can prevent it from spreading to other parts of the network, thereby containing the damage and preserving the integrity of unaffected areas.
- Compliance Assurance: For organizations operating under regulatory frameworks, firewalls play a crucial role in compliance. They provide detailed logging and monitoring of network traffic, which is essential for auditing and reporting purposes. This functionality helps organizations meet industry standards such as GDPR, HIPAA, and PCI-DSS by ensuring that security policies are consistently applied and documented.
- Application Protection: Advanced firewalls, such as Next-Generation Firewalls (NGFWs), offer application-layer filtering capabilities. This allows them to inspect the traffic associated with specific applications and enforce policies based on application behavior. By blocking harmful applications and allowing only legitimate ones, these firewalls enhance protection against sophisticated attacks that target application vulnerabilities.
- Intrusion Detection and Prevention: Modern firewalls often incorporate Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) to detect and respond to suspicious activities. These systems analyze traffic patterns and can automatically take action to block potential threats, providing an additional layer of defense against complex attack vectors.
- Unified Threat Management: Many firewalls offer integrated threat management features, combining various security functions into a single solution. This includes antivirus protection, anti-spam, VPN support, and more. By consolidating multiple security measures into one device, firewalls simplify security management and enhance overall network protection.
Network Layer vs. Application Layer Inspection
| Aspect | Network Layer Inspection | Application Layer Inspection |
| Layer | Operates at Layer 3 (Network Layer) | Operates at Layer 7 (Application Layer) |
| Focus | Analyzes packet headers and routing information | Examines the payload of data packets and specific application content |
| Traffic Filtering | Filters based on IP addresses, port numbers, and routing information | Filters based on application protocols (e.g., HTTP, FTP, SMTP) and behavior |
| Detection Capability | Effective for blocking unauthorized access, DDoS attacks, and port scans | Detects sophisticated threats, such as SQL injection, XSS, and malware |
| Performance Impact | Generally lower impact on performance due to simpler rules and checks | Potentially higher impact due to deeper, more resource-intensive analysis |
| Examples | IP address and port-based filtering, access control lists (ACLs) | Web traffic filtering, email content inspection, application-specific rules |
| Use Case | Broad network protection, blocking known malicious IPs, and ensuring network availability | Detailed examination of application behavior, protecting against application-layer vulnerabilities |
| Strengths | Provides quick, efficient traffic management and network security | Offers precise, context-aware protection and detailed threat prevention |
| Limitations | Limited insight into the actual content and context of traffic | Requires more computational resources and can be slower due to in-depth analysis |
| Example Technologies | Traditional firewalls, routers with access control lists | Next-Generation Firewalls (NGFWs), Web Application Firewalls (WAFs) |
| Granularity | Less granular; focuses on broad traffic characteristics | More granular; focuses on specific application behaviors and protocols |
| Security Posture | Suitable for general network security and handling straightforward attacks | Essential for securing applications and dealing with complex, targeted attacks |
The Importance of NAT and VPN
In the realm of network security and management, Network Address Translation (NAT) and Virtual Private Networks (VPNs) play crucial roles in safeguarding data and enhancing privacy.
Network Address Translation (NAT) is a method used to map private IP addresses to a public IP address. This technique offers several benefits:
- IP Address Conservation: NAT allows multiple devices on a local network to share a single public IP address. This conserves the limited pool of available public IP addresses.
- Enhanced Security: By masking internal IP addresses, NAT adds a layer of obscurity, making it more difficult for external attackers to identify and target internal devices.
- Simplified Network Management: NAT enables seamless internal network expansions without needing changes to the external IP address configuration.
Virtual Private Networks (VPNs) provide a secure method for accessing and transmitting data across potentially unsafe networks, such as the internet. Key advantages include:
- Data Encryption: VPNs encrypt data traffic, ensuring that sensitive information remains confidential and secure from eavesdroppers.
- Remote Access: VPNs facilitate secure remote access to an organization’s internal network, allowing users to work from various locations without compromising security.
- Bypass Geo-Restrictions: VPNs enable users to bypass geographical content restrictions by masking their actual location with a virtual IP address.
Next Generation Firewalls and Beyond
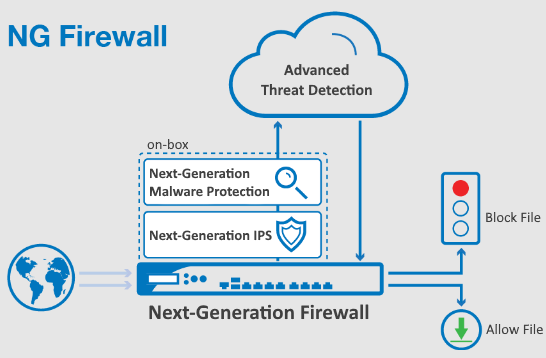
Next Generation Firewalls (NGFWs) have revolutionized network security by surpassing traditional firewalls with their advanced capabilities. Unlike their predecessors, NGFWs offer comprehensive threat intelligence, deep packet inspection, and application-level control. These cutting-edge features enable NGFWs to detect and mitigate sophisticated attacks that evade conventional security measures. As cyber threats become increasingly complex, NGFWs are evolving to incorporate machine learning and behavioral analytics, enhancing their ability to predict and counteract emerging threats. The future of firewalls will likely see further advancements, integrating even more refined techniques to safeguard networks against a dynamic threat landscape.
“Evolving from simple packet filters, modern firewalls now perform deep packet inspection to thwart sophisticated cyber threats.”
Conclusion
In an era where digital threats are both pervasive and sophisticated, the role of a firewall remains indispensable. By providing a robust barrier between internal networks and external threats, firewalls are crucial for safeguarding sensitive data and maintaining network integrity. They have evolved from simple packet filters to advanced systems capable of deep packet inspection and threat intelligence. Understanding the capabilities and limitations of different types of firewalls—from packet filtering to Next Generation Firewalls (NGFWs)—ensures a well-rounded security strategy. As technology progresses, staying informed about advancements in firewall technology is essential for effective defense against the ever-evolving landscape of cyber threats.
“A robust firewall forms the cornerstone of any comprehensive security strategy, protecting sensitive data from external intrusions.”
Frequently Asked Questions (FAQ) about Firewalls
- What is a firewall?
- A firewall is a network security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
- How does a firewall work?
- A firewall works by filtering traffic at the network’s entry and exit points, allowing or blocking data packets based on established security criteria.
- Why is a firewall important?
- A firewall is crucial for protecting your network from unauthorized access, cyber threats, and ensuring the integrity of your data.
- What are the different types of firewalls?
- The main types include packet filtering firewalls, stateful inspection firewalls, proxy firewalls, and next-generation firewalls (NGFW).
- What is a next-generation firewall (NGFW)?
- A next-generation firewall (NGFW) is an advanced version of traditional firewalls that provides deeper inspection capabilities and better security against modern threats.
- Can a firewall protect against all types of cyber threats?
- While a firewall is a critical component of network security, it should be used in conjunction with other security measures, such as antivirus software and intrusion detection systems.
- What is the difference between hardware and software firewalls?
- Hardware firewalls are standalone devices that protect the entire network, while software firewalls are installed on individual devices to protect them from threats.




great blog very nice articles I will follow you continuously sohbet odaları