What is Network Access Control?

What if every device attempting to access your network was evaluated with meticulous precision? Network Access Control (NAC) does exactly that, standing guard over your digital landscape, allowing only trusted entities to interact with sensitive data. It’s more than just a security layer; it’s a powerful defense mechanism in an age where cyber threats lurk at every corner. By implementing Network Access Control, organizations gain unparalleled control over who enters their network and how. Ready to understand how NAC not only enhances security but also fortifies your organization’s resilience? Let’s explore the transformative potential of NAC.
Table of Contents
Network Access Control Definition
Network Access Control (NAC) is a comprehensive security solution designed to regulate, monitor, and enforce policies on devices connecting to a network. At its core, Network Access Control serves as a gatekeeper, scrutinizing every connection attempt to ensure only authorized users and compliant devices gain access. This technology assesses devices against pre-defined policies, examining factors such as device health, user credentials, and compliance with security standards.
By doing so, NAC provides organizations with precise control over their networks, enabling them to limit entry points, minimize security risks, and maintain a secure digital environment. In today’s complex IT landscape, where cyber threats continue to evolve, Network Access Control remains essential. It offers a layered defense, ensuring that access is selectively granted and constantly monitored, strengthening an organization’s overall security posture.
Why Is Network Access Control (NAC) Important?
- Enhanced Security: Network Access Control prevents rogue devices and malicious actors from infiltrating the network, reducing the risk of breaches that could compromise sensitive data.
- Operational Control: By offering visibility over every connected device, NAC enables administrators to identify, isolate, or remove any device that deviates from security policies, providing full command over the network landscape.
- Regulatory Compliance: Industries like healthcare and finance rely on NAC to meet stringent data protection requirements. NAC’s detailed monitoring and policy enforcement simplify compliance with regulations and audits.
- Rapid Threat Response: With Network Access Control, organizations gain real-time insights that allow them to respond swiftly to suspicious activity, reducing the time between detection and resolution.
- Resource Efficiency: By automatically managing and controlling device access, NAC reduces the workload on IT teams, freeing up resources to focus on more strategic initiatives.
With Network Access Control, businesses can safeguard their networks by dynamically managing access rights based on user identity and device health.
What Are the Main Advantages of Network Access Control Solutions?
1- Increased Network Visibility
Network Access Control (NAC) enhances network security by providing unprecedented visibility into every connected device and user. This visibility allows IT teams to see who and what is accessing the network at any given moment, uncovering potential vulnerabilities before they can be exploited. Through Network Access Control, organizations gain a comprehensive, real-time overview of network activity, ensuring that every connection is verified and accounted for. This increased transparency not only strengthens security but also enables swift responses to unusual or suspicious behavior, effectively minimizing risks and reinforcing the integrity of the network environment.
2- Improved Cybersecurity
Network Access Control (NAC) significantly enhances an organization’s cybersecurity posture by meticulously regulating access to critical resources. By implementing NAC, businesses can ensure that only authenticated and compliant devices are allowed on the network. This not only mitigates the risk of unauthorized access but also protects against potential malware infiltration. With continuous monitoring and real-time analytics, Network Access Control swiftly identifies and neutralizes threats, providing a robust defense against evolving cyberattacks. By fostering a secure environment, NAC empowers organizations to safeguard sensitive data and maintain operational integrity, ensuring that cybersecurity remains a top priority in an increasingly complex digital landscape.
3- More Effective Compliance
Network Access Control (NAC) plays a pivotal role in achieving more effective compliance with industry regulations and standards. By enforcing access policies and continuously monitoring network activity, NAC ensures that only authorized users and compliant devices are permitted entry. This level of scrutiny helps organizations meet stringent requirements set forth by regulations such as GDPR, HIPAA, and PCI-DSS. Moreover, Network Access Control provides detailed logs and reports, which are essential for audits and assessments. By automating compliance measures, organizations can minimize human error, streamline processes, and demonstrate their commitment to safeguarding sensitive information, ultimately enhancing their overall risk management strategy.
4- Cost Savings
Implementing Network Access Control (NAC) can lead to significant cost savings for organizations. By proactively managing device access and enforcing compliance policies, NAC reduces the likelihood of costly data breaches and security incidents. These breaches often result in hefty fines, legal fees, and reputational damage. Additionally, Network Access Control streamlines IT operations by automating device authentication and monitoring, which lessens the burden on IT personnel and optimizes resource allocation. This efficiency translates into lower operational costs. Ultimately, investing in NAC not only safeguards sensitive data but also fortifies an organization’s financial health, making it a smart strategic choice.
5- Ease of Control
Network Access Control (NAC) simplifies the management of network security, providing an unparalleled ease of control for IT administrators. With centralized oversight, NAC enables seamless monitoring of all connected devices, ensuring that each access request is scrutinized and authenticated. This streamlined approach not only enhances operational efficiency but also empowers administrators to swiftly respond to security threats and policy violations. By automating access controls, Network Access Control reduces the complexity traditionally associated with network management, allowing teams to focus on strategic initiatives rather than firefighting vulnerabilities. Ultimately, NAC fosters a more secure environment while simplifying the intricate dance of network oversight.
How Does Network Access Control Work?
- Device Identification and Authentication: When a device attempts to connect to the network, NAC first identifies it through a variety of methods, such as MAC address, IP address, and user credentials. This initial step ensures that only recognized devices can seek access.
- Policy Enforcement: After identification, NAC evaluates the device against predefined security policies. These policies may include criteria like device health (e.g., updated antivirus software, operating system patches) and compliance with organizational security standards. If the device meets the requirements, access is granted; if not, access can be denied or limited.
- Network Segmentation: NAC can segment the network into different zones, allowing organizations to isolate devices based on their security posture or role. For example, guest devices may only have access to the internet, while corporate devices can access internal resources.
- Continuous Monitoring: Once a device is connected, NAC continuously monitors its behavior. This real-time oversight detects anomalies, unauthorized activities, or policy violations, enabling prompt responses to potential threats.
- Remediation Actions: If a connected device is found to be non-compliant or exhibits suspicious behavior, NAC can automatically take remediation actions. These actions may include isolating the device, sending alerts to administrators, or redirecting the device to a quarantine area for further investigation.
- Reporting and Auditing: NAC solutions generate detailed logs and reports of all access attempts, device statuses, and compliance audits. This data is essential for identifying trends, ensuring compliance with regulations, and refining security policies over time.
Capabilities of Network Access Control
Network Access Control (NAC) encompasses a robust suite of capabilities that fortify organizational security and enhance network management. At its core, NAC provides device identification and authentication, ensuring that only trusted endpoints can access sensitive resources. It evaluates device compliance by assessing security configurations, patch levels, and antivirus status, thereby preventing vulnerabilities from entering the network.
Another critical capability of Network Access Control is network segmentation. By dividing the network into distinct zones, NAC minimizes the potential attack surface and restricts lateral movement of threats. This segmentation enables organizations to enforce tailored access policies, granting users permissions based on their roles and device status.
Additionally, NAC offers continuous monitoring of network traffic, enabling real-time detection of suspicious activities. This proactive oversight allows for immediate remediation actions, such as isolating compromised devices or alerting IT personnel. Ultimately, Network Access Control not only strengthens security but also streamlines operational efficiency, making it an essential component of modern cybersecurity strategies.
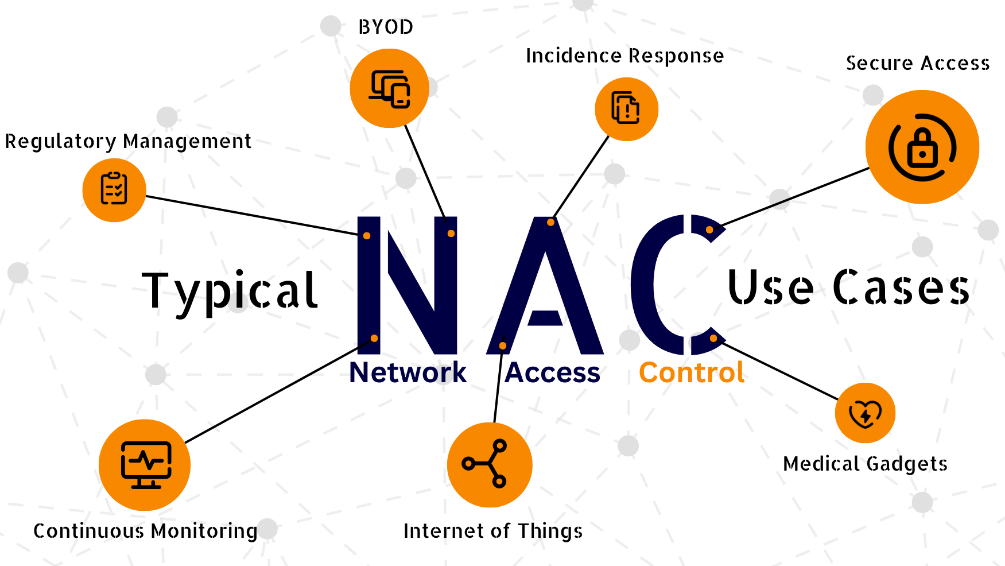
What Are the Major NAC Use Cases?
- Guest Access Management: In environments like corporate offices or hospitals, NAC can provide secure, isolated network access to guests, ensuring they don’t have access to sensitive resources.
- Bring Your Own Device (BYOD) Control: With the increase in personal devices used for work, NAC helps secure network access by enforcing policies for these devices, reducing potential vulnerabilities.
- Internet of Things (IoT) Security: As IoT devices proliferate, NAC solutions help monitor and manage access for these devices, ensuring they meet compliance standards and don’t become points of entry for attacks.
- Network Segmentation for Critical Assets: By segmenting networks, NAC can limit access to critical assets like servers, ensuring only specific, approved users have entry, reducing the risk of insider threats.
What Are the Main Types of Network Access Control?
Port-based NAC
Port-based NAC is a fundamental approach within the realm of Network Access Control that secures network access at the switch port level. By employing protocols such as 802.1X, it ensures that devices are authenticated before gaining access to the network. This method allows organizations to enforce stringent security policies by requiring devices to prove their identity and compliance status. If a device fails to meet the specified criteria, access can be denied or restricted. Additionally, port-based NAC facilitates network segmentation, isolating devices based on their trust levels. This proactive control mechanism significantly mitigates the risk of unauthorized access and potential security breaches, reinforcing the integrity of the network environment.
Device-based NAC
Device-based NAC is a critical component of Network Access Control that focuses on assessing the security posture of individual devices before granting access to the network. This approach gathers detailed information about each device, including its operating system, installed software, and security configurations. By evaluating compliance with organizational policies, device-based NAC ensures that only trusted and secure devices are allowed on the network. If a device is deemed non-compliant—due to outdated software or insufficient security measures—access can be restricted or denied altogether. This proactive method not only enhances network security but also streamlines the management of connected devices, reducing vulnerabilities and mitigating potential threats effectively.
User-based NAC
User-based NAC is a vital strategy within Network Access Control that emphasizes the authentication and authorization of individual users rather than merely focusing on devices. This approach ensures that access to network resources is granted based on user identity and assigned roles, thereby enforcing role-based access control (RBAC). By verifying credentials and evaluating user permissions, user-based NAC restricts access to sensitive information and applications, aligning with organizational policies. This tailored access not only enhances security but also fosters accountability, as each user’s actions can be traced back to their specific credentials. As a result, organizations can better safeguard their data and maintain a robust security posture in an increasingly complex threat landscape.
Agent-based NAC
is an innovative approach within Network Access Control that utilizes lightweight software agents installed on devices to monitor and enforce security policies. These agents continuously assess the health and compliance of endpoints, gathering real-time data on configurations, software versions, and security settings. By doing so, agent-based NAC enables organizations to implement granular access controls based on the current state of each device. If a device becomes non-compliant, the agent can initiate remediation actions, such as restricting access or prompting the user to update their system. This proactive monitoring significantly enhances security by ensuring that only secure and compliant devices are granted network access, thereby reducing the risk of potential breaches.
Agentless NAC
is a dynamic approach within Network Access Control that eliminates the need for installing software agents on endpoints. Instead, it leverages existing network protocols and technologies to assess devices as they connect to the network. By utilizing techniques such as passive scanning and authentication via DHCP and RADIUS, agentless NAC provides visibility into all connected devices without disrupting user operations. This method is particularly advantageous for organizations seeking to streamline deployment and minimize management overhead. Despite its non-intrusive nature, agentless solutions still deliver effective security by enforcing compliance and access policies, thereby ensuring that only authorized and secure devices can access critical network resources.
Cloud-based NAC
represents a transformative shift in Network Access Control, harnessing the power of cloud computing to deliver scalable and flexible security solutions. By centralizing access management in the cloud, organizations can monitor and control network access across distributed environments, including remote locations and mobile devices. This approach offers real-time visibility and rapid deployment, enabling businesses to adapt to evolving security threats swiftly. With cloud-based NAC, policies can be updated dynamically, ensuring compliance across various devices without the burden of maintaining on-premises infrastructure. Additionally, this model facilitates collaboration among teams, enhancing security posture while simplifying management in an increasingly mobile and interconnected world.
Policy-based NAC
is a strategic framework within Network Access Control that centers around the establishment and enforcement of predefined security policies. By defining specific criteria for device access, organizations can ensure that only compliant endpoints are granted network entry. This method evaluates various factors, including user roles, device health, and security posture, to determine access rights dynamically. With policy-based NAC, administrators can quickly respond to emerging threats, modifying policies as necessary to address vulnerabilities. This adaptive approach not only enhances security but also promotes operational efficiency by automating access decisions based on a robust set of guidelines, thereby reducing the risk of human error in access management.
In an era where cyber threats are rampant, Network Access Control serves as the first line of defense, ensuring only authorized users access critical resources.
Conclusion
In conclusion, Network Access Control is an essential component of modern cybersecurity strategies, offering organizations a robust framework to safeguard their networks. By employing various NAC methods, such as agent-based, user-based, and policy-based approaches, businesses can enforce stringent access controls tailored to their unique environments. As cyber threats continue to evolve, the importance of comprehensive visibility and control cannot be overstated. Implementing effective Network Access Control solutions not only mitigates risks but also enhances operational efficiency. Ultimately, a proactive stance on network access ensures that organizations can protect sensitive data while maintaining a flexible and secure network infrastructure.
Effective Network Access Control empowers organizations to maintain security and compliance, allowing them to adapt to an ever-changing digital landscape.
FAQs related to Network Access Control:
- What is Network Access Control (NAC)?
Network Access Control (NAC) is a security solution that enforces policies for controlling access to network resources based on user identity, device compliance, and security policies. - Why is Network Access Control important?
Network Access Control is crucial for enhancing security, ensuring compliance, and providing visibility into network activity by allowing only authorized devices and users to access sensitive information. - What are the main types of Network Access Control?
The main types of Network Access Control include agent-based NAC, agentless NAC, cloud-based NAC, and policy-based NAC, each offering unique features for managing network security. - How does Network Access Control improve cybersecurity?
Network Access Control enhances cybersecurity by monitoring devices, enforcing security policies, and preventing unauthorized access, thereby reducing the risk of breaches and data loss. - Can Network Access Control help with compliance?
Yes, Network Access Control helps organizations meet compliance requirements by ensuring that only compliant devices access the network and by providing detailed audit trails of user activity. - What are the benefits of implementing Network Access Control?
Benefits of Network Access Control include increased network visibility, improved cybersecurity, effective compliance management, cost savings, and ease of control over network resources. - How does Policy-based Network Access Control work?
Policy-based Network Access Control works by establishing predefined security policies that determine access rights based on factors like user roles, device health, and compliance status.