How to Install Metasploit: A Step-by-Step Guide

Are you ready to fortify your cybersecurity defenses and stay ahead of potential threats? Install Metasploit, the ultimate tool for penetration testing and vulnerability assessment, and transform your approach to security. Imagine having the power to identify and exploit system weaknesses before malicious actors do. With Metasploit, this isn’t just a possibility—it’s a reality. Don’t leave your network’s safety to chance. Dive into the world of Metasploit and discover how this sophisticated framework can revolutionize your security strategy. The first step to a more secure future starts with a single action: Install Metasploit today.
Table of Contents
What is Metasploit Framework
The Metasploit Framework is a robust and versatile platform used for penetration testing and vulnerability assessment. Developed by Rapid7, it provides a comprehensive suite of tools designed to identify and exploit security weaknesses in networks, applications, and systems. By simulating real-world attacks, Metasploit enables security professionals to evaluate their defenses and enhance their protection strategies. Whether you are conducting a thorough security audit or testing the resilience of your network, install Metasploit to gain invaluable insights and bolster your cybersecurity measures. Its extensive library of exploits and payloads makes it an indispensable asset for anyone serious about safeguarding their digital environment.
Prerequisites and Requirements To Install Metasploit
Before you install Metasploit, it is imperative to ensure that your system meets certain prerequisites and requirements to guarantee a seamless installation and optimal performance. The Metasploit Framework supports a variety of operating systems, including Windows, Linux, and macOS. For Windows users, compatibility starts from Windows 7 and above. On the Linux front, distributions such as Ubuntu, Debian, and CentOS are fully supported.
Supported Operating Systems and Minimum System Requirements
The Metasploit Framework is compatible with multiple operating systems, including Windows, Linux, and macOS. For Windows users, the framework supports versions from Windows 7 onwards. Linux users can install it on distributions such as Ubuntu, Debian, and CentOS.
Minimum system requirements include:
| Category | Requirements |
|---|---|
| Supported Operating Systems | Windows 7 and above Ubuntu – Debian – CentOS – macOS |
| Processor | Minimum 2 GHz, recommended 2.5 GHz or higher |
| RAM | Minimum 4 GB, recommended 8 GB |
| Storage | At least 1 GB of available disk space, recommended 5 GB |
| Internet Connection | Required for initial download, updates, and new modules |
| Graphics | Not specifically required, basic graphics sufficient |
| Additional Software | Ruby (version 2.6 or later) Database (PostgreSQL preferred) |
Disable Anti-virus Software
When engaged in advanced cybersecurity assessments like installing Metasploit, it’s often necessary to disable anti-virus software temporarily. This step ensures that the tool can operate without interference, allowing for comprehensive testing and identification of vulnerabilities within a system’s defenses. However, it’s crucial to exercise caution and re-enable anti-virus software promptly after completing the necessary tasks to maintain the integrity and security of the system.
Disable Firewalls
In cybersecurity operations, disabling firewalls temporarily, especially when installing Metasploit, can be necessary to conduct thorough vulnerability assessments. Firewalls, while essential for network security, can sometimes hinder tools like Metasploit from probing system defenses effectively. By strategically disabling firewalls, cybersecurity professionals ensure unrestricted access for comprehensive testing and identification of potential vulnerabilities. It’s imperative, however, to reinstate firewall protections promptly after completing assessments to maintain network integrity and safeguard against potential threats.
Obtain Administrator Privileges
Administrator privileges are essential for installing and configuring Metasploit. These permissions ensure that the framework can modify system settings and access necessary directories. Without administrative rights, the installation process might encounter significant hurdles.
| Operating System | Privilege Name | Description |
| Windows | Administrator | Required for installing software, modifying system settings, and accessing restricted directories. |
| Allows management of user accounts and security policies. | ||
| Linux | Root or Superuser | Essential for executing commands that modify system configurations and install software packages. Use sudo for administrative tasks on Ubuntu, Debian, or CentOS. |
| Provides full access to system resources and configurations. | ||
| Enables installation and management of software packages via package managers (e.g., apt, yum). |
Installing the Metasploit Framework on Windows
The Metasploit Framework stands as a cornerstone in the arsenal of cybersecurity professionals, facilitating comprehensive penetration testing and vulnerability analysis. Installing Metasploit on Windows involves a series of essential steps:
- Prepare Your Environment: Ensure your Windows system meets the prerequisites for Metasploit installation, including the latest service packs, sufficient RAM (recommended 4GB or more), and available disk space.
- Download the Installer: Obtain the latest Metasploit installer package from the official Rapid7 website or reputable sources. Check the integrity of the download to safeguard against tampering.
- Run the Installer: Execute the installer with administrative privileges to initiate the installation process. This step launches the Metasploit Setup Wizard.
- Follow the Installation Wizard: Navigate through the installation wizard, which guides you through crucial setup decisions such as installation directory, components to install (such as the database and auxiliary modules), and integration options with other tools.
- Configure Settings: During installation, configure settings like network interface bindings, database connections (typically PostgreSQL), and user account settings as per your operational requirements.
- Verify and Test: Once installation completes, verify the installation integrity by launching Metasploit and performing initial tests to ensure all components function as expected.
- Update and Secure: Regularly update Metasploit to leverage the latest features and security patches. Configure firewalls and security software to allow Metasploit to operate effectively without compromising system security.
1- Download the Windows Installer.
2- After downloading the installer, locate the file, right-click, and select Run as Administrator.
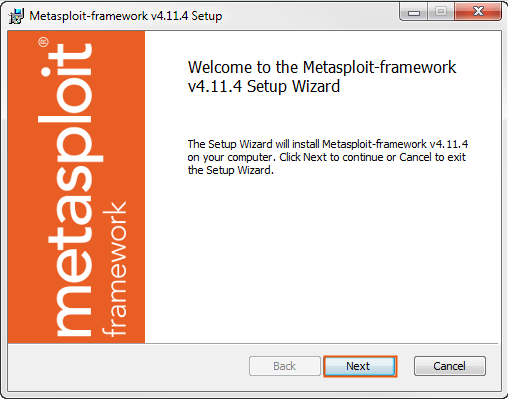
3- When the Setup screen appears, click Next to continue.
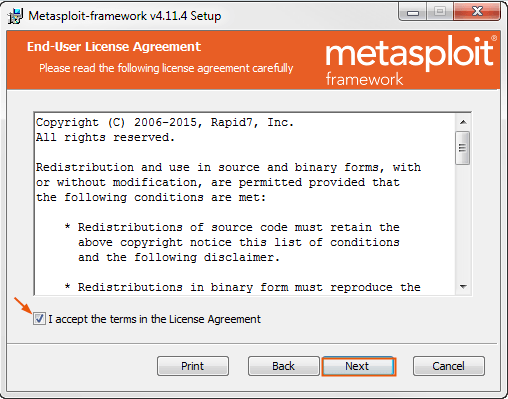
4- Read the license agreement and select the I accept the license agreement option. Click Next to continue.
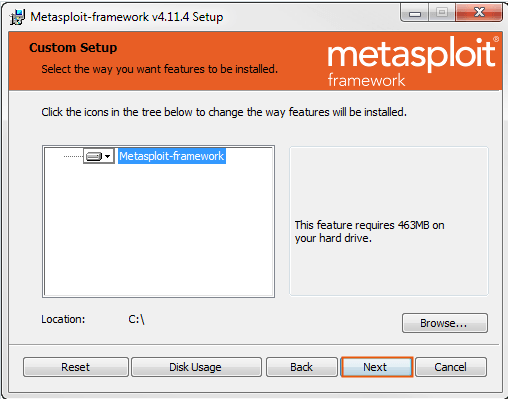
5- Browse to the location where you want to install the Metasploit Framework. By default, the framework is installed on the C:\ Metasploit-framework directory. Click Next to continue.

6- Click Install.
7- The installation process can take 5-10 minutes to complete. When the installation completes, click the Finish button.
8- To launch msfconsole after the installation completes, run the following from the command line:

Installing the Metasploit Framework on Linux
The Metasploit Framework is an indispensable tool for cybersecurity professionals, providing robust capabilities for penetration testing and vulnerability assessment. Follow these detailed steps to install Metasploit on an Ubuntu system:
1- System Preparation:
Update your package list and upgrade existing packages to ensure your system is current:
sudo apt-get update sudo apt-get upgrade
Install essential dependencies required for Metasploit to function correctly:
sudo apt-get install -y curl gnupg2 postgresql postgresql-contrib libpq-dev
2- Download Metasploit:
Download the Metasploit installer script from Rapid7’s repository:
curl https://raw.githubusercontent.com/rapid7/metasploit-framework/master/msfinstall --output msfinstall
3- Install Metasploit:
Make the installer script executable:
chmod +x msfinstall
Run the installer script with superuser privileges to start the installation process:sudo ./msfinstall
4- Configure PostgreSQL:
Start the PostgreSQL service to enable database operations:
sudo service postgresql start
Enable PostgreSQL to start on boot:
sudo systemctl enable postgresql
Switch to the PostgreSQL user and create a new user and database for Metasploit:
sudo -u postgres createuser msf -P sudo -u postgres createdb -O msf msf_database
5- Initialize Metasploit Database:
Initialize the database for Metasploit to set up the necessary configurations:
msfdb init
Verify that the database connection is working correctly by checking the status:
msfdb status
6- Verify Installation:
Launch Metasploit to ensure that all components are properly installed and functional:
msfconsole
Run the following command within Metasploit to confirm the database connection:
db_status
7- Update and Secure:
Regularly update Metasploit to keep up with the latest security patches, exploits, and modules: msfupdate
Configure your system’s firewall to allow Metasploit to function while maintaining security. For example, you can allow specific ports used by Metasploit:
sudo ufw allow 5432/tcp
sudo ufw allow 55553/tcp
sudo ufw enable
Conclusion
In the ever-evolving landscape of cybersecurity, installing Metasploit emerges as a critical strategy for proactive defense. This versatile tool empowers cybersecurity professionals with advanced capabilities for penetration testing and vulnerability assessment. By leveraging Metasploit, organizations can bolster their security frameworks, identifying and remedying potential weaknesses before they are exploited. Regular updates and meticulous attention to security protocols are essential to maximize the efficacy of Metasploit in safeguarding digital infrastructures against emerging threats.
FAQs on Installing Metasploit
- 1. What is Metasploit?
- 2. Why should I install Metasploit?
- 3. What are the system requirements for installing Metasploit?
- 4. How can I install Metasploit on Linux?
- 5. How do I install Metasploit on Windows?
- 6. Is it possible to install Metasploit on macOS?
- 7. What are the common issues faced during Metasploit installation?
- 8. How can I verify the Metasploit installation?
- 9. Can I install Metasploit on a virtual machine?
- 10. How do I keep Metasploit updated?




