What Is Ransomware : Keep Your Digital World Secure

Imagine waking up to find your computer system locked and your critical data inaccessible, held hostage by a shadowy digital extortionist. This is the unsettling reality of ransomware, a pervasive cyber threat that targets individuals and organizations with merciless precision. Intrigued by the audacity of these cybercriminals? Alarmed by the potential vulnerability of your own data? The rise of ransomware has not only escalated the stakes in the cybersecurity arena but also underscored the imperative need for robust defense mechanisms. Don’t wait until it’s too late; delve into the world of ransomware and arm yourself with knowledge to protect against this formidable menace.
Table of Contents
What Is Ransomware?

Ransomware is a malicious software designed to infiltrate computer systems, encrypt valuable data, and hold it hostage until a ransom is paid. This insidious threat often enters through deceptive emails or compromised websites, swiftly locking users out of their files. With encryption methods becoming increasingly sophisticated, ransomware can cripple businesses, disrupt services, and cause substantial financial loss. The attackers typically demand payment in cryptocurrency, making the transactions nearly impossible to trace. Understanding ransomware and its mechanisms is crucial in fortifying defenses against this pervasive digital menace.
How Does Ransomware Work?
File Encryption
a process that converts data into an unreadable format, accessible only with a unique decryption key. When ransomware infiltrates a system, it quickly encrypts critical files, rendering them useless to the user. This encryption can extend to documents, images, databases, and even entire drives. The attackers then demand a ransom for the decryption key, exploiting the victim’s desperation to regain access. The strength and complexity of modern encryption algorithms used by ransomware make it nearly impossible to break without the key, amplifying the urgency and severity of the threat.
Ransom and Demands
it doesn’t just encrypt files; it also delivers a menacing ultimatum. The attackers present a ransom note, typically demanding payment in cryptocurrency for anonymity. These demands can range from a few hundred to millions of dollars, depending on the target’s perceived ability to pay. The note often includes dire warnings of data destruction or increased ransom if payment is delayed. Victims are left with a grim choice: comply with the criminals or risk losing invaluable data. This high-stakes extortion underscores the ruthless efficiency and psychological manipulation that make ransomware a formidable cyber threat.
Ransomware Attacks
Malspam
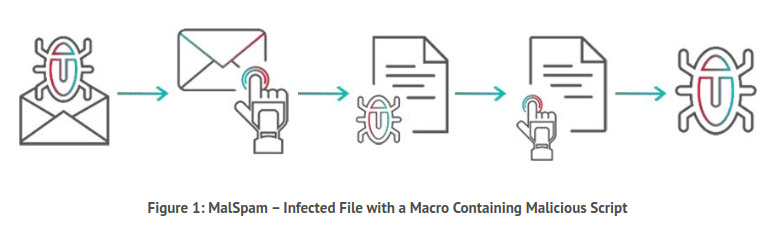
a portmanteau of “malicious spam.” These deceptive emails masquerade as legitimate communications, enticing recipients to click on infected links or download harmful attachments. Once the payload is unleashed, ransomware rapidly encrypts critical files, locking users out. Malspam exploits human vulnerability, relying on curiosity, urgency, or fear to trick recipients. Cybercriminals continuously refine their tactics, making malspam increasingly sophisticated and harder to detect. Recognizing and avoiding malspam is essential in defending against the pervasive threat of ransomware, which can devastate both individuals and organizations.
Malvertising
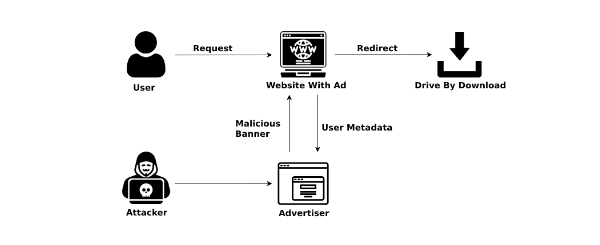
Malvertising, or malicious advertising, is a stealthy conduit for ransomware. Cybercriminals infiltrate legitimate online ad networks with infected ads that, when clicked, redirect users to malicious websites. These sites automatically download and execute ransomware, often without the user’s knowledge. Malvertising exploits the trust users place in reputable websites and ad networks, making it a particularly insidious threat. The widespread reach of online advertisements amplifies the potential impact, affecting thousands of unsuspecting users. Vigilance and robust cybersecurity measures are crucial to mitigate the risks posed by malvertising and the relentless advance of ransomware.
Common Ransomware Attack Targets
- Healthcare Facilities: Hospitals, clinics, and medical research centers are prime targets due to their critical need for immediate access to patient records and medical data. Disruptions can delay treatments and endanger lives, making the healthcare sector a high-value target for ransomware criminals.
- Educational Institutions: Universities and schools hold vast repositories of student records, research data, and administrative information. An attack can cripple educational operations, affect student privacy, and disrupt research projects, creating a compelling reason for attackers to target these institutions.
- Financial Services: Banks, investment firms, and insurance companies are rich in sensitive client data, financial transactions, and proprietary information. The potential for significant financial gain makes them prime targets for ransomware attacks that can lead to major economic losses and regulatory scrutiny.
- Government Agencies: Government entities manage essential services, public records, and sensitive national security information. An attack on these institutions can have severe repercussions, including national security risks and public safety concerns, which can amplify the impact of ransomware.
- Small Businesses: Despite their size, small businesses often lack comprehensive cybersecurity measures, making them vulnerable. Attackers exploit these weaknesses, knowing that small businesses may be less prepared to handle a ransomware attack and may be more likely to pay the ransom to avoid prolonged downtime.
- Retail Sector: Retailers process substantial amounts of customer data, including payment information and personal details. Ransomware attacks in this sector can lead to data breaches, financial loss, and damage to consumer trust, making it a lucrative target for cybercriminals.
- Manufacturing Industry: Manufacturing companies depend on complex supply chains and production processes. An attack that disrupts operations or locks critical data can halt production, leading to significant financial losses and supply chain disruptions, making the sector a high-value target.
- Legal Firms: Law firms store sensitive client information, case files, and confidential communications. An attack can compromise client confidentiality, disrupt legal proceedings, and expose the firm to legal and financial liabilities, increasing the attractiveness of ransomware attacks on these entities.
- Energy and Utilities: Energy providers and utility companies manage critical infrastructure that is essential for public and industrial operations. Ransomware attacks can disrupt power supplies, water services, and other essential utilities, causing widespread public and economic impact.
- Media and Entertainment: This sector holds valuable intellectual property, including unreleased content, scripts, and proprietary media assets. Ransomware attacks can hold this content hostage, impacting release schedules and leading to significant financial and reputational damage.
Types of Ransomware
1- Scareware
Scareware is a deceptive variant of ransomware designed to exploit users’ fears. Instead of encrypting files, it bombards victims with alarming messages, falsely claiming their system is infected or compromised. These messages often mimic legitimate security alerts and prompt users to download fraudulent antivirus software or pay for unnecessary services. By preying on the user’s anxiety, scareware aims to coerce payment or installation of additional malicious software. While it may not cause the same direct data loss as other types of ransomware, its psychological manipulation and financial exploitation make it a dangerous threat.
2- Screen Locking
Screen locking paralyzes a victim’s computer by taking over the screen and blocking access to all applications and files. Unlike file-encrypting variants, screen-locking ransomware does not encrypt data but instead displays a full-screen message that prevents users from interacting with their system. This message often contains alarming warnings or demands a ransom payment to regain access. The primary goal of screen-locking ransomware is to coerce victims into paying quickly to restore their access, leveraging the immediate and complete denial of functionality to increase urgency and compliance.
3- Encrypting Ransomware
Encrypting ransomware encrypts files on a victim’s computer, rendering them inaccessible. Unlike other types of ransomware, this variant employs advanced encryption algorithms to scramble data, making it unreadable without a decryption key. The attackers demand a ransom, typically paid in cryptocurrency, in exchange for the decryption key needed to restore access. This method is highly effective because it directly targets the victim’s ability to use critical data, causing significant operational disruptions and financial loss. The severity of the impact often forces victims to consider paying the ransom to recover their essential files.
4- Some Emerging Threats
The landscape of ransomware is continuously evolving, with new and sophisticated threats emerging regularly. One notable trend is the rise of ransomware-as-a-service (RaaS), which allows even low-skilled cybercriminals to deploy attacks using commercial kits. Another emerging threat involves double extortion, where attackers not only encrypt data but also exfiltrate it, threatening to release it publicly if the ransom is not paid. Additionally, ransomware targeting cloud services and virtual environments is on the rise, exploiting vulnerabilities in these rapidly expanding technologies. The increasing complexity and adaptability of these threats highlight the need for advanced and proactive cybersecurity measures.
Ransomware Detection
- Behavioral Analysis: Monitor for unusual file access patterns, such as rapid encryption of multiple files, which can indicate ransomware activity.
- Signature-Based Detection: Utilize up-to-date antivirus software to identify known ransomware signatures and malware variants. Regular updates are essential to keep pace with evolving threats.
- Anomaly Detection: Implement systems that recognize deviations from normal network behavior, such as unexpected data encryption or abnormal network traffic, which may signal a ransomware intrusion.
- Heuristic Analysis: Employ advanced algorithms that evaluate the potential risk of files and applications based on their behavior and characteristics, rather than relying solely on known signatures.
- Endpoint Monitoring: Regularly inspect endpoints for signs of ransomware infection, such as unusual file changes or unauthorized access attempts.
- File Integrity Monitoring: Track changes to critical system files and directories to detect unauthorized modifications typical of ransomware attacks.
- Network Traffic Analysis: Analyze network traffic for suspicious patterns, such as unusual data transfers or connections to known malicious IP addresses, which may indicate ransomware.
- User Behavior Analytics: Monitor user activity for signs of phishing attempts or unauthorized access that could precede a ransomware attack.
- Dark Web Monitoring: Keep an eye on dark web forums and marketplaces where stolen data or ransomware tools might be traded, providing early warning of potential threats.
How To Respond to a Ransomware Attack?

Check for Scareware
To effectively address ransomware threats, it’s crucial to check for scareware:
- Monitor System Behavior: Watch for unusual system performance or unexpected changes in system settings indicative of ransomware or scareware activity.
- Examine Pop-Up Alerts: Look for alarming messages or pop-ups that claim your system is compromised and urge immediate action or payment.
- Verify Source Authenticity: Assess the legitimacy of any security alerts or prompts by cross-referencing with reputable security sources.
- Scan for Malicious Software: Use a trusted antivirus program to detect and remove any scareware that may be mimicking legitimate security tools.
- Review Recent Downloads: Investigate any recent software installations or downloads that might have introduced scareware.
Consult an Expert
consulting an expert is a critical step. Ransomware attacks can be complex and sophisticated, requiring specialized knowledge for effective resolution. An experienced cybersecurity professional can perform a comprehensive analysis, identify the strain of ransomware, and assess the damage. They provide guidance on whether to negotiate with attackers or pursue other recovery options. Additionally, experts can assist in system decryption, data recovery, and strengthening security measures to prevent future attacks. Relying on a seasoned specialist ensures a more strategic and informed approach to managing and mitigating the impact of ransomware.
How to Remove Ransomware?
- Isolate the Infected System: Disconnect the infected device from the internet and any local networks immediately. This step prevents the ransomware from spreading to other systems or encrypting additional files.
- Identify the Ransomware Variant: Use specialized tools or consult cybersecurity professionals to identify the specific variant of ransomware. Knowing the strain can guide the choice of decryption tools and removal methods. Resources like ID Ransomware can help in identifying the malware.
- Run a Full System Scan: Deploy a reputable antivirus or anti-malware tool to conduct a comprehensive scan of the system. The tool will detect and remove known ransomware files and associated malware. Ensure the software is updated to recognize the latest threats.
- Restore from Backup: If you have clean, unaffected backups, use them to restore encrypted files. Before doing so, ensure that the backup is free from ransomware and that the infection has been completely removed from the system.
- Check for Residual Threats: After initial removal, run additional scans to confirm that all traces of ransomware are eradicated. Check for unusual system behavior, and inspect areas such as startup programs and scheduled tasks for hidden threats.
- Update and Secure: Apply all available security patches and updates to your operating system and applications. Ensure that your antivirus and firewall are up-to-date to defend against future attacks. Consider implementing endpoint protection solutions and a comprehensive backup strategy.
- Consult Cybersecurity Experts: For complex infections or if you are unsure about any steps, consult cybersecurity professionals. They can provide in-depth analysis, decrypt files if possible, and advise on enhancing your security posture.
- Educate and Prevent: Educate yourself and your team about ransomware and other cyber threats. Implement best practices for cybersecurity, such as regular updates, cautious handling of email attachments, and secure password management.
“Effective defense against ransomware requires a proactive blend of technology, strategy, and employee education.”
How To Protect Your Business From Ransomware?
- Regular Updates: Ensure that all software, including operating systems and applications, are consistently updated with the latest security patches. This helps close vulnerabilities that ransomware can exploit.
- Robust Antivirus Protection: Deploy advanced antivirus solutions that offer real-time protection and regularly scan for ransomware and other malware. Keep the software up-to-date to counter emerging threats.
- Data Backup: Regularly back up critical data and store backups in a secure, offline location. This ensures that you can restore your data in the event of a ransomware attack without paying a ransom.
- Network Segmentation: Segment your network to limit the spread of ransomware within your organization. Implement strict access controls and monitor network traffic for suspicious activity.
- Employee Training: Educate employees about recognizing phishing emails and avoiding malicious links or attachments. Regular training can reduce the likelihood of ransomware infections initiated through social engineering.
- Strong Authentication: Use multi-factor authentication (MFA) to secure access to critical systems and data. This adds an extra layer of protection against unauthorized access.
- Incident Response Plan: Develop and regularly test an incident response plan to quickly address and mitigate ransomware attacks. Ensure that all staff are familiar with the procedures to follow in case of an incident.
How to Prevent Ransomware Attacks?
1- Update Frequently
Regularly updating your software and systems is a crucial defense against ransomware. Ransomware frequently exploits known vulnerabilities in outdated applications and operating systems. By applying the latest patches and updates, you close security gaps that could be leveraged by malicious actors. These updates often include fixes for critical vulnerabilities that ransomware could exploit to gain unauthorized access. Ensure that both your operating system and all installed software are kept up-to-date, and enable automatic updates when possible. This proactive measure significantly reduces the risk of ransomware infiltrating your network and causing potential damage.
2- Authenticate Software
Authenticating software is a pivotal step in defending against ransomware. Ensure that all applications are sourced from reputable vendors and verified before installation. Use digital signatures and checksums to confirm the integrity and authenticity of software. This process prevents the introduction of ransomware through malicious or tampered software. Avoid downloading applications from unknown or suspicious websites, as these can be vehicles for ransomware. Implement software integrity monitoring tools to continuously verify that installed applications remain unaltered. By rigorously authenticating software, you mitigate the risk of ransomware infiltrating your systems and safeguard your data.
3- Install Antivirus Protection
Installing robust antivirus protection is crucial in safeguarding against ransomware. A reliable antivirus solution offers real-time scanning, detecting and neutralizing ransomware before it can compromise your system. Regular updates to the antivirus software are essential, as they ensure defense against the latest ransomware variants and evolving threats. Configure the antivirus to conduct periodic scans of your entire system and files to enhance detection capabilities. By maintaining current and comprehensive antivirus protection, you significantly mitigate the risk of ransomware infections and bolster your overall cybersecurity posture.
4- Whitelist Software
Whitelisting software is an effective strategy to combat ransomware by controlling which applications are permitted to run on your system. By maintaining a list of approved, trusted programs, you block unauthorized software from executing, including potential ransomware. This approach minimizes the risk of ransomware infections by ensuring that only vetted applications can operate. Regularly review and update the whitelist to include legitimate new software while excluding any potential threats. Whitelisting enhances security by reducing the attack surface and preventing unknown or suspicious applications from executing, thereby fortifying your defenses against ransomware.
5- Back Up Your Data
Regularly backing up your data is a vital defense against ransomware. In the event of a ransomware attack, having up-to-date backups ensures that your critical files remain intact and accessible, even if they are encrypted by the malicious software. Store backups in a secure, off-site location to protect them from being compromised along with your primary data. Employ automated backup solutions to maintain consistent and reliable copies of your data, and verify that these backups are functioning correctly. By implementing a robust backup strategy, you can mitigate the impact of ransomware and facilitate a swift recovery from any potential attacks.
6- Educate Employees
Educating employees is a crucial line of defense against ransomware. Training staff to recognize phishing attempts, suspicious links, and malicious attachments can significantly reduce the risk of ransomware infections. Regularly update training programs to address evolving tactics used by cybercriminals. Simulate phishing attacks to reinforce awareness and assess preparedness. Foster a culture of cybersecurity vigilance, encouraging employees to report potential threats immediately. By equipping your team with knowledge and practical skills, you fortify your organization’s defenses and diminish the likelihood of a successful ransomware attack.
7- Use a Comprehensive Security Solution
Employing a comprehensive security solution is essential for safeguarding against ransomware. This approach integrates multiple layers of protection, including firewalls, intrusion detection systems, and advanced threat protection. A holistic security solution continuously monitors network traffic, identifies anomalous behavior, and neutralizes potential threats before they can inflict damage. Regular updates and real-time threat intelligence enhance its effectiveness against emerging ransomware variants. By consolidating security measures into a unified system, organizations can achieve a more robust defense, ensuring comprehensive coverage and significantly reducing the risk of ransomware infiltration.
8- Ransomware Prevention, Simplified
Ransomware prevention can be streamlined by focusing on key strategies. Start by keeping all software and systems up-to-date to close security vulnerabilities. Implement robust antivirus solutions and configure them to run regular scans. Regularly back up important data and store these backups securely offline. Educate employees about recognizing phishing attempts and suspicious activities. Employ a comprehensive security solution to monitor and protect against threats. Lastly, use multi-factor authentication to secure access to sensitive information. By integrating these straightforward measures, organizations can effectively shield themselves from ransomware attacks and minimize potential damage.
“Ransomware attacks are not just a technical issue but a profound challenge to organizational resilience and data integrity.”
Conclusion
In conclusion, defending against ransomware requires a multifaceted approach that integrates proactive and reactive measures. Regular updates, robust antivirus solutions, and comprehensive security strategies form the cornerstone of an effective defense. Educating employees and implementing secure backup protocols further enhance resilience against ransomware threats. By adopting these practices, organizations can mitigate the risk and impact of ransomware attacks, ensuring greater security and operational continuity. Vigilance and preparedness are key to safeguarding valuable data and maintaining a secure digital environment.
“Preventing ransomware is about more than just installing software; it’s about building a culture of vigilance and preparedness.”
(FAQ) about Ransomware
- What is ransomware?
- Ransomware is a type of malicious software that encrypts a victim’s data, demanding a ransom payment to restore access.
- How does ransomware work?
- Ransomware typically infects systems through phishing emails, malicious links, or software vulnerabilities, encrypting files and demanding payment for decryption.
- What are common signs of a ransomware attack?
- Signs of ransomware include unexpected file encryption, ransom notes on the screen, and system performance issues.
- How can I prevent a ransomware attack?
- To prevent ransomware attacks, regularly update software, use comprehensive security solutions, back up data, and educate employees about cybersecurity best practices.
- What should I do if I’m a victim of ransomware?
- If affected by ransomware, disconnect from the network, consult with cybersecurity experts, and avoid paying the ransom. Restore files from backups if available.
- How can I remove ransomware from my system?
- Removing ransomware involves running reputable antivirus scans, employing specialized decryption tools, and, if necessary, restoring systems from clean backups.
- Are there tools to detect ransomware?
- Yes, there are advanced security solutions and tools designed to detect ransomware through behavior analysis and threat intelligence.
- What are the emerging threats in ransomware?
- Emerging threats in ransomware include more sophisticated encryption methods, targeted attacks on specific industries, and ransomware-as-a-service models.




Sugar Defender is an innovative supplement designed to promote balanced blood sugar levels and support metabolic wellness.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.