What is an intrusion prevention systems : Essential Tips

Are your digital assets truly secure against the relentless tide of cyber threats? Intrusion Prevention Systems offer more than just alerts—they provide an active defense, repelling intruders before they can inflict damage. Imagine a fortress that not only detects but neutralizes threats in real-time. As cyber adversaries become increasingly sophisticated, the need for advanced security measures grows ever more pressing. Discover how Intrusion Prevention Systems can revolutionize your cybersecurity strategy, ensuring robust protection and peace of mind. Embrace cutting-edge technology and safeguard your digital future with unparalleled precision.
Table of Contents
What is an Intrusion Prevention System?
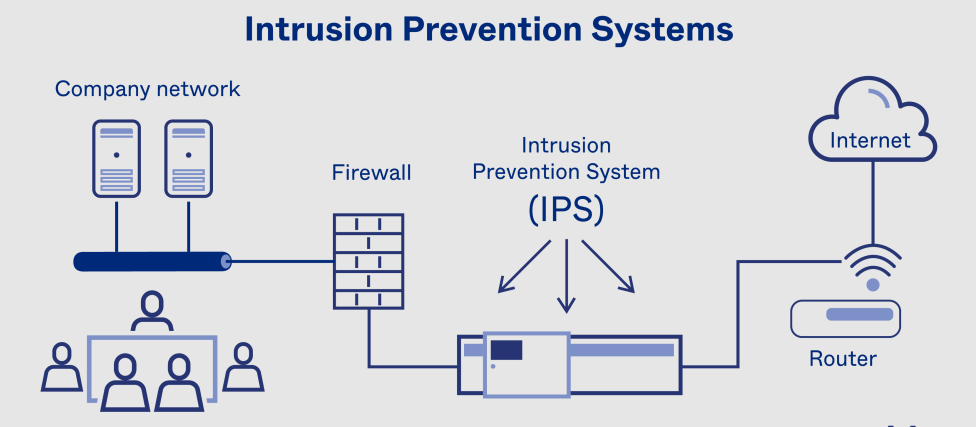
An Intrusion Prevention System (IPS) is a critical cybersecurity technology designed to detect and thwart malicious activities in real-time. Unlike passive monitoring tools, Intrusion Prevention Systems actively analyze network traffic, identifying and blocking suspicious behavior before it infiltrates the network. These systems leverage advanced techniques such as signature-based detection and anomaly detection to provide robust protection. By continuously scanning for threats, Intrusion Prevention Systems ensure that only legitimate and safe data packets are allowed, safeguarding sensitive information and maintaining the integrity of digital infrastructure.
How Does an Intrusion Prevention System Work?
Intrusion Prevention Systems (IPS) are sophisticated tools designed to proactively safeguard networks against malicious activities. They operate through a multi-faceted approach, ensuring comprehensive protection. Here’s a detailed look at how they function:
- Traffic Monitoring: Intrusion Prevention Systems continuously monitor all network traffic, inspecting every data packet that enters or leaves the network. This persistent vigilance allows the IPS to maintain a real-time understanding of network activity.
- Signature-Based Detection: The system uses a database of known attack signatures—patterns or sequences associated with specific threats. When incoming data matches a signature, the IPS immediately identifies it as a potential threat and blocks it. This method is highly effective against recognized attacks.
- Anomaly Detection: By establishing a baseline of normal network behavior, Intrusion Prevention Systems can identify anomalies—activities that deviate from the established norm. This approach is crucial for detecting zero-day exploits and new, previously unknown threats that do not match any existing signatures.
- Policy Enforcement: Intrusion Prevention Systems enforce security policies that define acceptable and unacceptable network behavior. These policies are tailored to an organization’s specific needs and can block or allow traffic based on predefined criteria, such as IP addresses, ports, and protocols.
- Real-Time Response: Upon detecting a threat, Intrusion Prevention Systems take immediate action to neutralize it. Actions can include dropping malicious packets, resetting connections, blocking offending IP addresses, and generating alerts to notify network administrators. This rapid response minimizes the potential impact of the threat.
- Deep Packet Inspection (DPI): Intrusion Prevention Systems utilize DPI to thoroughly examine the contents of data packets beyond just the headers. This detailed inspection helps identify complex threats that may be hidden within the packet payload.
- Logging and Reporting: Every detected threat and corresponding action is logged for further analysis. These logs provide valuable insights into attack patterns and help in refining the IPS’s detection capabilities. Regular reports are generated to keep administrators informed about the security status of the network.
Types of Intrusion Prevention Systems
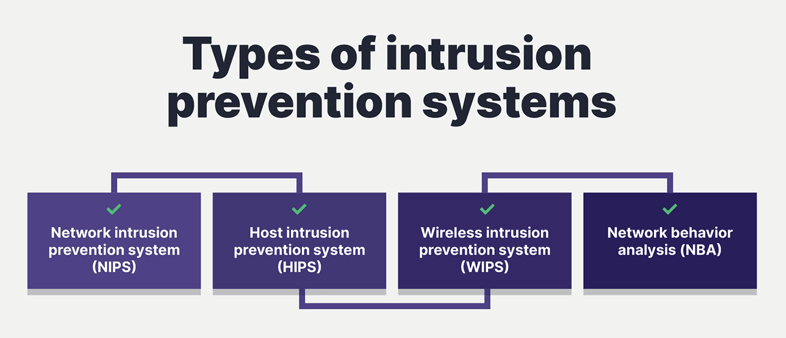
1- Network-based IPS (NIPS)
Network-based IPS (NIPS) is a critical component of Intrusion Prevention Systems that provides comprehensive protection across an entire network. Deployed at strategic points such as network perimeters or data centers, NIPS inspects all incoming and outgoing traffic in real-time. It identifies and mitigates threats by analyzing data packets for malicious patterns or behaviors. Leveraging techniques like signature-based and anomaly-based detection, Network-based IPS acts as a gatekeeper, blocking harmful traffic before it reaches sensitive systems. Its broad coverage ensures robust network security, safeguarding against a diverse range of cyber threats.
2- Host-based IPS (HIPS)
Host-based IPS (HIPS) is a specialized form of Intrusion Prevention Systems designed to protect individual devices such as servers, workstations, and endpoints. Installed directly on these hosts, HIPS monitors and analyzes system activities to detect and block potential threats. By focusing on the operating system and application behaviors, Host-based IPS can prevent attacks that bypass network-level defenses. It uses a combination of signature-based and behavioral analysis to identify suspicious activities and enforce security policies. This localized protection ensures that each device is shielded from intrusions, providing an additional layer of defense against cyber threats.
3- Wireless IPS (WIPS)
Wireless IPS (WIPS) is a pivotal component of Intrusion Prevention Systems specifically tailored to secure wireless networks. By continuously monitoring radio frequencies, WIPS detects unauthorized access points, rogue devices, and malicious activities within the wireless spectrum. It utilizes advanced techniques to analyze wireless traffic and identify anomalies that could indicate security breaches. Wireless IPS not only alerts administrators to potential threats but also takes proactive measures to mitigate risks, ensuring the integrity and confidentiality of wireless communications. Its role is crucial in maintaining a secure and resilient wireless network environment against evolving cyber threats.
4- Network Behavior Analysis (NBA) IPS
Network Behavior Analysis (NBA) IPS is an advanced type of Intrusion Prevention Systems focused on detecting unusual patterns within network traffic. Unlike traditional systems that rely solely on signature-based detection, NBA IPS employs sophisticated algorithms to establish a baseline of normal network behavior. By monitoring deviations from this baseline, Network Behavior Analysis IPS can identify potential threats that may not match known attack signatures. This approach is particularly effective against sophisticated or emerging threats, offering dynamic protection by recognizing anomalies that could indicate malicious activities. Through its proactive analysis, NBA IPS enhances network security and resilience against complex cyber threats.
What are the Benefits of an Intrusion Prevention System?
- Proactive Threat Mitigation: By actively analyzing and blocking malicious activities in real-time, Intrusion Prevention Systems prevent potential breaches before they can disrupt operations or compromise sensitive data.
- Enhanced Detection Capabilities: Utilizing a combination of signature-based, anomaly-based, and behavior-based detection methods, these systems identify a broad spectrum of threats, including sophisticated and previously unknown attack vectors.
- Reduced False Positives: Intrusion Prevention Systems are engineered to differentiate between legitimate and harmful traffic, minimizing false alarms and ensuring that only genuine threats are addressed, thereby reducing unnecessary interruptions.
- Regulatory Compliance: Implementing an IPS supports adherence to industry standards and regulations for data security, such as GDPR or HIPAA, helping organizations avoid compliance issues and associated penalties.
- Increased Network Visibility: Continuous monitoring and deep packet inspection offer comprehensive insights into network traffic patterns, enabling the identification of potential vulnerabilities and optimizing security configurations.
- Improved Incident Response: By providing detailed logs and alerts, Intrusion Prevention Systems enhance the ability to respond quickly and effectively to security incidents, facilitating swift containment and remediation.
- Adaptive Security: Modern Intrusion Prevention Systems can adapt to evolving threats by updating threat signatures and detection algorithms, ensuring continued protection against emerging cyber risks.
Why is an Intrusion Prevention System Important?
Intrusion Prevention Systems are crucial in today’s complex cybersecurity landscape due to their proactive defense capabilities. They provide real-time monitoring and immediate response to potential threats, preventing malicious activities before they can compromise critical systems. Intrusion Prevention Systems employ advanced detection methods, including signature-based and anomaly-based analysis, to safeguard against both known and emerging threats. Their ability to block harmful traffic and enforce security policies helps maintain the integrity of sensitive data and ensures compliance with regulatory standards. In essence, Intrusion Prevention Systems offer essential protection, minimizing risk and enhancing overall network resilience.
How Does an Intrusion Prevention System Fit Within My Existing Security Infrastructure?
Adaptable Integration: Designed to integrate with other security technologies, Intrusion Prevention Systems can be deployed within various network environments, including on-premises, cloud, and hybrid infrastructures, adapting to diverse security needs.
Complementary Layer: Intrusion Prevention Systems act as an additional layer of security, complementing firewalls and antivirus solutions. They provide deeper analysis and real-time threat prevention, addressing vulnerabilities that other tools may miss.
Centralized Management: Modern Intrusion Prevention Systems offer centralized management consoles, allowing for cohesive monitoring and control alongside existing security solutions. This integration simplifies the administration and correlation of security events.
Enhanced Visibility: By incorporating Intrusion Prevention Systems, you gain greater visibility into network traffic and potential threats. This detailed insight helps in refining security policies and improving incident response strategies.
Policy Enforcement: Intrusion Prevention Systems can be configured to enforce security policies across the network, ensuring consistent protection and compliance with regulatory requirements.
Recommended for You
To enhance your cybersecurity posture, consider incorporating Intrusion Prevention Systems (IPS) into your security infrastructure. These advanced solutions offer real-time protection by identifying and blocking malicious activities before they can cause harm. Explore various IPS options tailored to different needs, including network-based, host-based, and wireless systems. Each type provides unique advantages, ensuring comprehensive defense across all aspects of your network. Evaluate how Intrusion Prevention Systems can integrate with your existing security measures to bolster protection and maintain robust defenses against evolving cyber threats. Investing in a reliable IPS will fortify your network security and safeguard your valuable assets.
Related Solutions and Products
| Solution/Product | Description |
| Firewall Systems | Firewalls regulate and filter network traffic based on security policies, blocking unauthorized access and mitigating external threats. They serve as the first line of defense, complementing Intrusion Prevention Systems by providing a barrier against unauthorized access. |
| Endpoint Protection Platforms | These platforms offer protection for individual devices against malware, ransomware, and other threats. They include antivirus, anti-malware, and behavior monitoring features, working in tandem with Intrusion Prevention Systems to secure endpoints from internal and external attacks. |
| Security Information and Event Management (SIEM) | SIEM solutions aggregate, analyze, and correlate data from various security sources. They provide real-time alerts and detailed insights into network activities, enhancing the effectiveness of Intrusion Prevention Systems by offering a holistic view of security events and trends. |
| Virtual Private Networks (VPNs) | VPNs encrypt data transmitted over public networks, ensuring secure remote access and protecting sensitive information from interception. They complement Intrusion Prevention Systems by securing communication channels, reducing the risk of data breaches and unauthorized access. |
| Network Access Control (NAC) | NAC solutions enforce policies to control which devices can connect to the network. They ensure that only compliant devices gain access, enhancing the effectiveness of Intrusion Prevention Systems by minimizing the risk of security breaches from non-compliant or compromised devices. |
| Advanced Threat Protection (ATP) | ATP solutions provide enhanced detection and response capabilities for sophisticated threats. They employ advanced techniques such as machine learning and behavioral analysis to identify and mitigate zero-day exploits and advanced persistent threats, augmenting the defenses of Intrusion Prevention Systems. |
| Data Loss Prevention (DLP) | DLP tools monitor and protect sensitive data from unauthorized access or leaks. By controlling data flows and enforcing policies, they work alongside Intrusion Prevention Systems to safeguard critical information and ensure compliance with data protection regulations. |
NSX Advanced Threat Prevention
NSX Advanced Threat Prevention integrates seamlessly with Intrusion Prevention Systems to offer a robust security solution for modern networks. By leveraging sophisticated analytics and machine learning, it provides advanced threat detection and automated response capabilities. NSX Advanced Threat Prevention not only enhances traditional Intrusion Prevention Systems by identifying and mitigating sophisticated threats but also ensures comprehensive visibility and control over network traffic. Its ability to analyze behavior and enforce granular security policies helps safeguard against evolving cyber threats. This integration strengthens overall network defenses, making it an essential component of a multi-layered security strategy.
In the ever-evolving landscape of cybersecurity, Intrusion Prevention Systems are the vigilant sentinels that stand guard against emerging threats, ensuring that potential breaches are thwarted before they can impact the network.
Conclusion
In conclusion, Intrusion Prevention Systems are a critical element in the cybersecurity arsenal, offering proactive protection against a wide array of threats. Their real-time threat detection and mitigation capabilities enhance network security by addressing vulnerabilities before they can be exploited. By integrating Intrusion Prevention Systems with complementary security solutions, organizations can achieve a layered defense strategy that provides comprehensive protection. As cyber threats continue to evolve, the role of Intrusion Prevention Systems in maintaining robust security and ensuring operational integrity remains indispensable. Investing in these systems is essential for safeguarding sensitive information and maintaining a resilient cybersecurity posture.





YoI wanted to express my admiration for your incredible article. The clarity and expertise you demonstrate on this subject are truly impressive. If you don’t mind, I would love to subscribe to your feed to stay informed about your future posts. Thank you very much for your outstanding work, and please keep it up. My site. Come by 광주 초원의집
Hello, mateI was immediately captivated by your blog post! Ever since I discovered your blog, I have been completely absorbed in all of your articles. The compelling content you offer has left me craving for more. I have subscribed to your RSS feed and am eagerly anticipating your future updates!Adios. my web page.. Come by 토지노사이트
Hi thereWhile exploring a different website, we stumbled upon this webpage that instantly grabbed our interest. We are genuinely amazed by what we have witnessed thus far and eagerly anticipate staying informed about your upcoming content. We are thrilled to further explore your website and discover all the incredible offerings it holds. My site.. Come by 빅벳사이트.com
Hello thereYour blog post was truly captivating! Since stumbling upon your blog, I have been completely absorbed in your other articles. The compelling content you provide has left me craving for more. I have subscribed to your RSS feed and am eagerly looking forward to your upcoming updates!Stay well. my page. Come by 카지노 커뮤니티
GreetingsYour blog post was a delight to read! Since stumbling upon your blog, I have been completely absorbed in your other articles. The captivating content you provide has left me eagerly craving for more. I have subscribed to your RSS feed and am eagerly looking forward to your future updates! my page.. Come by 토렌트사이트
Great post! I really enjoyed reading it. I was wondering if you could provide more information on this topic. I would greatly appreciate it if you could elaborate a bit further. Thank you so much!Later, gator. my web page.. Come by 오산 레깅스룸
Hey thereDuring our exploration of a new website, we stumbled upon a webpage that instantly captivated our attention. We are thoroughly impressed with what we have discovered thus far and eagerly anticipate your upcoming updates. We are thrilled to delve deeper into your website and discover all the fantastic features it has to offer. my page Come by 재테크 종류
We stumbled upon this webpage on another site and were intrigued to explore further. I’m really liking what I see, so I’ll be keeping up with your updates. Looking forward to delving deeper into your website.Be good.
What’s up?While exploring a different website, we stumbled upon this webpage that instantly grabbed our interest. We are genuinely amazed by what we have witnessed thus far and eagerly anticipate staying informed about your upcoming content. We are thrilled to further explore your website and discover all the incredible offerings it holds.Bye-bye.
Howdy-doWhile exploring a new website, we came across a webpage that immediately caught our eye. We are incredibly impressed with what we have seen so far and eagerly look forward to your future updates. We are excited to further explore your website and uncover all the amazing features it has to offer.Adios.
I am deeply moved by your post, which has sparked a strong curiosity within me to delve deeper into the subject. Your extensive knowledge and insightful perspectives are truly admirable, and I sincerely value your unique point of view. Thank you for generously sharing your thoughts and taking the time to do so!Stay well.
SalutationsI really loved your post and found it incredibly insightful! I was wondering if you could provide more information on this topic. I would greatly appreciate it if you could go into more depth. Thank you so much for taking the time to share your thoughts!
Hi-yaYour outstanding article has truly impressed me, leaving a lasting impact. Your ability to explain complex ideas with clarity and expertise is remarkable. I look forward to subscribing to your updates and following your future work with great anticipation. Thank you for your exceptional contribution, and I wholeheartedly support and encourage you to continue excelling in all your endeavors.Until we meet again.
This is a topic that doesn’t get enough attention, so I’m glad you brought it up! For anyone who’s curious to learn more, https://ourfingers.com/ could be helpful.