The 12 Most Common Types of Malware
What would you do if your most valuable files vanished overnight, held hostage by an unseen adversary? In today’s hyperconnected world, malware isn’t just a distant threat—it’s a relentless force targeting businesses, individuals, and institutions alike. With countless types of malware—from cunning Trojans to devastating wiper malware—each one is engineered to infiltrate, disrupt, and exploit. These digital threats don’t discriminate; they prey on vulnerabilities both big and small. Understanding their tactics is the first step toward fortifying your defenses. Explore the 12 most common types of malware and discover how to safeguard what matters most in an ever-evolving cyber landscape.
Table of Contents
What Is Malware?

Malware, short for malicious software, is a sinister tool designed to infiltrate, disrupt, or exploit digital systems. It operates covertly, often undetected until significant damage has occurred. From stealing sensitive data to crippling entire networks, malware’s impact can be catastrophic. There are various types of malware, each engineered to execute specific malicious tasks. Ransomware holds data hostage, spyware silently harvests personal information, and worms spread autonomously, infecting every vulnerable node in their path. These threats evolve constantly, leveraging advanced techniques to bypass security measures. Recognizing the types of malware is essential to safeguarding personal and professional digital ecosystems.
In a world dominated by technology, understanding the types of malware is the first line of defense against digital threats.
What Are the Types of Malware ?
1. Ransomware
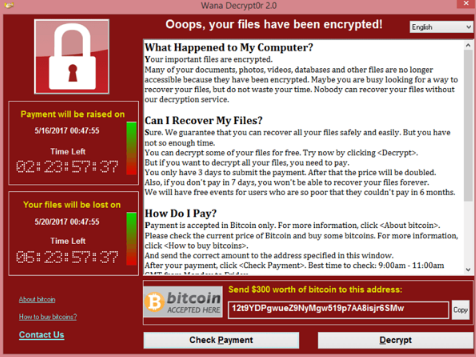
Ransomware is a particularly menacing type of malware, designed to lock users out of their own data until a ransom is paid. It typically encrypts files, rendering them inaccessible, and displays a message demanding payment—often in cryptocurrency—to restore access. Modern ransomware attacks are increasingly sophisticated, frequently employing double extortion tactics. This involves not only encrypting files but also stealing sensitive data, threatening to release it if the ransom is not paid. High-profile cases have paralyzed hospitals, corporations, and even entire municipal governments. Defending against ransomware requires proactive measures, such as maintaining regular backups, employing robust endpoint security, and exercising extreme caution with email attachments and downloads.
Examples of Ransomware
- WannaCry
One of the most infamous ransomware attacks, WannaCry spread rapidly in 2017, exploiting vulnerabilities in Microsoft Windows. It affected hundreds of thousands of computers across 150 countries, demanding payments in Bitcoin to restore access to encrypted files. - NotPetya
Originally appearing as a variant of Petya, NotPetya wreaked havoc in 2017, particularly in Ukraine. It was a destructive form of ransomware that, while still demanding payment, was primarily designed to cause widespread disruption rather than extort money. - CryptoLocker
CryptoLocker was one of the early examples of ransomware that encrypted files on the victim’s computer and demanded payment for the decryption key. It spread mainly via email attachments, targeting both individuals and businesses. - Ryuk
A highly targeted ransomware strain, Ryuk has been used in sophisticated attacks, often against large organizations, demanding massive ransoms. It typically uses other malware to gain access to a network before encrypting files and demanding payment. - Locky
First discovered in 2016, Locky ransomware was typically spread through phishing emails with infected attachments. Once executed, it encrypted files and demanded ransom in Bitcoin for their decryption. - Sodinokibi (REvil)
Sodinokibi, also known as REvil, is a highly effective ransomware-as-a-service (RaaS) used by cybercriminals. It has targeted large corporations, encrypting files and exfiltrating sensitive data, with the threat of publishing it unless the ransom is paid. - Maze
Maze is a notable ransomware variant that not only encrypts data but also steals it. It then threatens to release the stolen data unless the victim pays the ransom, contributing to the rise of double extortion tactics. - TeslaCrypt
TeslaCrypt primarily targeted gamers by encrypting files related to popular video games. After its release in 2015, it was eventually cracked, but not before causing significant damage to users’ files. - Jigsaw
Jigsaw is a form of ransomware that uses a frightening tactic: with each passing hour, it deletes a portion of the victim’s files until the ransom is paid. This relentless pressure made it infamous during its peak attacks. - Bad Rabbit
Bad Rabbit, which surfaced in 2017, spread via fake Adobe Flash updates and targeted systems in Russia and Ukraine. It encrypted files and demanded Bitcoin as ransom, resembling the earlier Petya ransomware but with different encryption techniques.
2. Fileless Malware
Fileless malware is a stealthy type of malware that leaves no tangible traces on a system’s hard drive, making it exceptionally difficult to detect. Instead of relying on traditional files, it exploits legitimate processes and resides in a system’s memory, leveraging tools like PowerShell or Windows Management Instrumentation (WMI) to carry out its malicious activities. This evasion tactic allows it to bypass many antivirus programs that rely on signature-based detection. Fileless malware often spreads through phishing attacks, malicious websites, or compromised software updates. Its ability to blend into normal system operations makes it a formidable adversary, emphasizing the need for behavior-based detection systems and rigorous endpoint monitoring.
Examples of Fileless Malware
- PowerShell-based Attacks
PowerShell is a powerful scripting tool used in Windows environments, and fileless malware often leverages it to execute malicious commands directly in memory. These attacks don’t leave traditional files behind and can evade detection by conventional antivirus software. One such example is the PowerShell Empire framework, which enables cybercriminals to execute malicious scripts without ever writing them to disk. - Cerber
Cerber is a well-known ransomware that, in some cases, uses fileless techniques. Instead of relying on traditional file-based payloads, it can execute its code directly in memory. This makes it harder for security software to detect and stop, as the malware doesn’t leave traces in the file system. - Powelike
Powelike is a malware campaign that uses fileless techniques to distribute a variety of malicious payloads, including spyware and Trojans. It typically exploits vulnerabilities in legitimate software (such as Microsoft Office) and uses scripting languages like PowerShell or VBScript to execute malware directly in memory. - FIN7 Attacks
The FIN7 hacker group, notorious for targeting financial institutions, frequently utilizes fileless malware techniques. They employ tools like PowerShell and Windows Management Instrumentation (WMI) to deliver payloads and maintain persistence without writing files to disk, thereby evading detection. - RATs (Remote Access Trojans)
Remote Access Trojans like Pupy and NJRat have been known to use fileless techniques. These malware variants enable attackers to gain remote control over infected systems and often execute their malicious commands in memory, avoiding detection by traditional signature-based antivirus tools. - Emotet
Originally a banking Trojan, Emotet evolved into a highly sophisticated malware-as-a-service platform. It can deploy fileless malware by using Macro-based attacks to trigger PowerShell scripts directly in memory, bypassing many security mechanisms and making detection challenging. - Dirobot (aka Backdoor.MACOS.Turla)
Dirobot is a backdoor malware that targets Mac systems, often using fileless methods to infiltrate and maintain control. It leverages legitimate system processes to execute malicious code directly in the memory, avoiding file-based signatures and remaining stealthy. - ReVuln
ReVuln is an advanced type of fileless malware that exploits vulnerabilities in common software, particularly web browsers and server platforms. It can run malicious code directly in memory, bypassing traditional security tools, and is often used in targeted attacks to steal sensitive information without leaving traces on disk.
3. Spyware
Spyware is a covert type of malware designed to monitor and collect sensitive information without the user’s knowledge. Operating silently in the background, it tracks activities such as browsing habits, keystrokes, passwords, and even financial transactions. Some variants can activate webcams or microphones, turning devices into surveillance tools. Spyware often infiltrates systems through malicious downloads, phishing links, or bundled software. While its primary use is data theft, it can also pave the way for identity theft, financial fraud, or corporate espionage. Detecting spyware requires vigilant monitoring and robust anti-malware tools. Regular software updates and cautious online behavior are vital in reducing exposure to this digital eavesdropper.
| Spyware Name | Description | Functionality |
| FinFisher (FinSpy) | A highly sophisticated spyware tool designed for surveillance, often used by government agencies and law enforcement. | Monitors user activity, captures keystrokes, records audio and video, and intercepts communications. It is highly stealthy, making it difficult to detect. |
| Pegasus | Developed by the Israeli company NSO Group, Pegasus is one of the most notorious spyware programs, capable of remote surveillance of mobile devices. | Gains full access to a victim’s phone, tracking texts, calls, photos, GPS location, and even activating the microphone or camera for real-time surveillance. |
| DarkHotel | Targets business executives and high-profile targets by exploiting vulnerabilities in hotel Wi-Fi networks to infect devices. | Steals sensitive business and personal information by gaining access to emails, passwords, and other confidential data. Often deployed via spear-phishing emails. |
| CoolWebSearch | A spyware that hijacks web browsers, alters homepages, and tracks user behavior to serve unwanted ads. | Collects browsing data, redirects searches to malicious sites, and gathers personal information for ad-serving purposes. |
| Keylogger-based Spyware | Spyware that records every keystroke typed on an infected device to capture sensitive information. | Tracks passwords, credit card numbers, emails, and private messages, allowing attackers to steal sensitive data without the user’s knowledge. |
| Red October | A highly advanced spyware operation discovered in 2012, which targeted government and diplomatic organizations worldwide. | Stealthily exfiltrates highly sensitive data, including documents and emails, from infected devices. Utilized in targeted cyber-espionage attacks. |
| ZeuS | Originally a banking Trojan, ZeuS also functions as spyware, stealing sensitive financial data and login credentials. | Logs keystrokes, monitors browser activity, and captures login information, often used for identity theft and financial fraud. |
| Tracking Cookies | Small pieces of data placed in a browser that track user activity, often without explicit consent. | Monitors online behavior for targeted advertising, collects personal data like browsing history, and tracks movements across multiple websites. |
| Spybot Search & Destroy | Originally a legitimate anti-spyware tool, certain versions have been modified to act as spyware, gathering system data under the guise of system optimization. | Detects spyware infections but can also collect personal information about the user, such as browsing habits and device configurations, when misused. |
| TAP (The Onion Router) | A type of spyware used in some surveillance operations, often seen as a method of monitoring Tor users or online activity. | Monitors and logs user activity, tracks online communications, and can compromise anonymous browsing sessions, often sending collected data to external servers. |
4. Adware
Adware is a disruptive type of malware that floods users with intrusive advertisements, often disguised as legitimate software. While it may seem relatively harmless compared to ransomware or spyware, adware poses significant risks. It can track user behavior, collecting data on browsing habits and preferences to deliver targeted ads—sometimes crossing the line into privacy invasion. Worse, some adware serves as a gateway to more dangerous malware, redirecting users to malicious websites or prompting downloads of harmful programs. Adware thrives on systems with outdated software or weak defenses, making regular updates and robust ad-blocking tools essential for prevention. Though often underestimated, adware’s ability to compromise security and privacy makes it more than just a nuisance.
| Adware Name | Description | Functionality |
| Fireball | A malicious adware known for hijacking browser settings and generating fraudulent ad traffic. | Redirects users to fake search engines, serves intrusive ads, and often collects sensitive information like browsing habits and search queries. |
| Conduit | A browser hijacker and adware that often bundles itself with other free software and modifies browser settings to show unwanted ads. | Changes the homepage, default search engine, and displays pop-up ads, often compromising the user’s privacy by collecting browsing data. |
| DollarRevenue | Adware that infects computers through bundled software. It is often installed without the user’s knowledge and floods the system with pop-up ads. | Delivers aggressive, unwanted ads and redirects search queries to affiliated sites, while tracking user interactions for marketing purposes. |
| V9.com | A type of adware that installs a toolbar and alters browser settings to serve advertisements on web pages and search results. | Displays ads, changes search engine settings, and tracks user browsing to serve personalized, yet unwanted, ads. |
| AdClicker | A malicious adware that displays pop-up ads and changes browser settings without the user’s consent, often bundled with free software. | Injects ads into web pages and tracks user activity for ad targeting, often leading to slow system performance and compromised privacy. |
| Softonic Downloader | While Softonic is a legitimate software distributor, the adware associated with it can hijack browser settings, inject ads, and track browsing history. | Tracks and collects user data, modifies system settings, and floods the browser with pop-up advertisements, often compromising system security. |
| Superfish | A form of adware pre-installed on certain Lenovo devices that intercepts HTTPS connections to display ads. | Injects targeted ads into web traffic by replacing legitimate content with sponsored ads, while compromising security by performing man-in-the-middle attacks. |
| MyWebSearch | An adware program that often installs as part of free software downloads, changing browser settings and displaying unwanted ads. | Alters browser homepage and search engine settings, displays intrusive pop-ups, and tracks user data for marketing purposes. |
| Babylon Toolbar | Often bundled with software downloads, this adware installs a toolbar that displays unwanted ads and alters browser search settings. | Injects ads into web pages, changes default search settings, and tracks user activity to serve targeted advertisements. |
| Coupon Server | A type of adware that claims to offer coupons and discounts but instead floods the system with pop-up ads. | Tracks browsing history and delivers unwanted, often irrelevant, ads and coupon offers, causing disruption to user browsing activities. |
5. Trojan
A Trojan is a deceptive type of malware that masquerades as legitimate software, tricking users into downloading and executing it. Named after the legendary Trojan horse, it gains access to a system by appearing harmless or even beneficial, often bundled with seemingly innocuous files or programs. Once activated, however, the Trojan opens a backdoor for cybercriminals, enabling them to steal sensitive data, install additional malware, or control the infected device remotely. Unlike viruses or worms, Trojans do not replicate themselves; instead, they rely on social engineering and user trust to spread. The best defense against Trojans is cautious downloading habits, vigilant email screening, and using reputable security software that can detect suspicious behaviors and files.
| Trojan Name | Description | Functionality |
| Emotet | A notorious Trojan originally designed for financial fraud, it has evolved into a highly effective malware delivery system. | Often used to deliver ransomware and other types of malware by exploiting email phishing attacks, it can steal banking credentials and personal data. |
| Zeus (Zbot) | One of the most infamous Trojans, primarily targeting banking information by infecting browsers and logging keystrokes. | Steals login credentials, financial data, and other sensitive information, typically used for banking fraud. |
| Dridex | A sophisticated Trojan that spreads primarily through phishing emails, targeting financial institutions and stealing banking details. | Infects systems to harvest financial data, deploys other malware, and can escalate privileges to further compromise the infected system. |
| FakeAV | A Trojan posing as an antivirus program, tricking users into thinking their computer is infected, leading them to download additional malicious software. | Creates a fake alert claiming the system is infected, urging users to install additional software that is itself malicious. |
| RAT (Remote Access Trojan) | A Trojan that gives attackers full remote control over an infected computer, allowing them to monitor, control, and manipulate it. | Enables cybercriminals to steal files, spy on users via webcams, record keystrokes, and deploy additional malware on the compromised system. |
| Shamoon | A destructive Trojan that was used in high-profile attacks against energy companies, designed to wipe out data and destroy systems. | Deletes files, overwrites the master boot record (MBR), and causes irreparable damage to infected systems, often used for political or ideological motives. |
| Andromeda | A Trojan used to deliver other malware such as ransomware and information stealers. It was often delivered through phishing emails and malicious downloads. | Establishes a backdoor into infected systems, enabling cybercriminals to distribute additional malware or steal sensitive data. |
| Conficker | A Trojan worm that infects Windows machines, creating a botnet used for spreading malware, stealing information, and launching DDoS attacks. | Disables security tools, creates a backdoor for remote access, and spreads rapidly via USB drives or network connections. |
| Locky | A Trojan primarily spread through phishing emails, used to deliver ransomware that encrypts user files and demands payment for their release. | Encrypts files on infected computers and demands a ransom payment, usually in cryptocurrency, for the decryption key. |
| Taterf | A Trojan used in advanced persistent threat (APT) attacks, often employed by state-sponsored actors to steal sensitive data from targeted networks. | Steals confidential data, enables remote access for espionage, and can spread across networks to other systems. |
6. Worms
Worms are a particularly dangerous type of malware known for their ability to self-replicate and spread autonomously across networks. Unlike viruses, worms do not require a host file to propagate; they exploit security vulnerabilities in software or operating systems to move from one device to another. Once inside, worms can cause widespread disruption, consume network bandwidth, and sometimes deliver additional payloads, like ransomware or spyware. Notable worms, such as WannaCry and Stuxnet, have caused billions in damage by infecting entire networks or critical infrastructure. Worms are especially effective in environments with outdated security systems, emphasizing the need for regular patching and strong network defenses to prevent their spread.
| Worm Name | Description | Functionality |
| Conficker | One of the most well-known worms, Conficker spreads through vulnerabilities in the Windows operating system. | Propagates rapidly across networks, disabling security features and allowing for further malware downloads or remote control of infected systems. |
| ILOVEYOU | A worm that spread via email with the subject line “I Love You,” infecting millions of computers in 2000. | Propagates through email attachments, corrupting files, stealing passwords, and sending itself to all contacts in the infected user’s address book. |
| Sasser | A worm that exploits a vulnerability in the Windows LSASS service, causing infected systems to crash and reboot repeatedly. | Scans for vulnerable machines, infects them, and spreads through open ports, often causing system instability or denial of service. |
| Blaster | A worm that exploited vulnerabilities in the Windows operating system to launch attacks against Microsoft’s DCOM RPC service. | Initiates a denial-of-service attack (DoS) against specific targets, while also spreading to other systems by exploiting the same vulnerability. |
| Code Red | A worm that targeted a vulnerability in Microsoft’s IIS web server, spreading rapidly in 2001. | Defaced websites, sent massive amounts of traffic to web servers, and launched denial-of-service attacks on specific websites. |
| SQL Slammer | A worm that spread rapidly by exploiting a vulnerability in Microsoft SQL Server 2000, causing massive global network disruptions in 2003. | Quickly spread across networks, causing SQL servers to crash and clogging up internet traffic, leading to widespread disruption. |
| Nimda | A worm that spread via email, network shares, and vulnerable web servers, infecting a wide range of systems in 2001. | Combined multiple propagation methods, including email attachments, network vulnerabilities, and compromised websites, spreading swiftly. |
| MyDoom | A worm that spread through email attachments and peer-to-peer networks, often used to launch Distributed Denial of Service (DDoS) attacks. | Creates a backdoor for remote access, spreads through infected emails, and launches DDoS attacks against specific websites or networks. |
| Storm Worm | A worm that spread via spam email messages disguised as legitimate news updates, often used to create botnets for further attacks. | Distributed massive amounts of spam, used to form botnets, and often used in cybercrime activities such as DDoS attacks and fraud. |
| WannaCry | A worm that spread through a Windows SMB vulnerability and was responsible for a massive global ransomware attack in 2017. | Exploits Windows vulnerabilities, encrypts user files, and demands a ransom in cryptocurrency for decryption, spreading rapidly across networks. |
7. Virus
A virus is one of the most well-known types of malware, capable of attaching itself to legitimate programs or files and spreading when those files are executed or shared. Once activated, it can corrupt or delete data, steal information, or damage system functionality. Viruses often require human intervention to spread, such as opening an infected email attachment or downloading compromised software. Modern viruses may even carry additional malicious payloads, delivering ransomware, spyware, or Trojans. While less autonomous than worms, viruses can be just as destructive, making regular software updates, cautious downloading practices, and comprehensive antivirus protection essential for defense. The lingering threat of viruses reminds us of the importance of maintaining secure digital habits.
| Virus Name | Description | Functionality |
| CIH (Chernobyl) | A destructive virus that infected Windows 95, 98, and ME systems, often spread through infected files and executable programs. | Corrupts or deletes files, overwrites the BIOS, and can cause the system to become unbootable, rendering it unusable. |
| Sasser | A virus that exploits vulnerabilities in the Windows operating system, specifically targeting the LSASS service. | Causes system crashes and reboots, and spreads across networks by exploiting unpatched vulnerabilities in Windows systems. |
| Marburg | A virus that spreads through infected email attachments and corrupts the Master Boot Record (MBR), making infected computers unbootable. | Deletes files, corrupts MBR, and renders infected systems unusable, often causing permanent data loss. |
| ZMist | A virus that is spread through infected email attachments or malicious websites, typically disguising itself as a useful file. | Installs itself on the victim’s system, steals information, and often spreads to other computers via network drives or email. |
| Stone Virus | A virus that infects executable files and spreads by attaching itself to these files, corrupting the files and causing system crashes. | Corrupts files and executable programs, rendering them unopenable, and spreads quickly across networks and infected devices. |
| Storm Worm | A virus that masquerades as an innocent file or email attachment and spreads via infected emails, often linked to malicious links and downloads. | Creates a botnet by infecting computers, spreads by sending out spam emails, and is used to perform DDoS attacks and data theft. |
| Invader | A virus that infects the Windows operating system and is spread through file-sharing applications and email attachments. | Infects executable files, causes system instability, and may damage files or steal sensitive information from the compromised system. |
| Sasser | A virus that exploits vulnerabilities in Microsoft’s LSASS (Local Security Authority Subsystem Service), spreading via the internet. | Reboots infected systems repeatedly, causing widespread network disruptions, and can lead to massive system crashes if not patched. |
| Cameleon | A virus that spreads via email, and once executed, it attaches itself to files and sends copies of itself to all the contacts in the infected system. | Infects files, often uses social engineering to spread, and overloads email inboxes by sending itself to all contacts. |
| Love Bug (ILOVEYOU) | A virus that spread via email, using an enticing subject line (“I love you”) to trick users into clicking on the infected attachment. | Overwrites files, sends itself to the user’s address book, and spreads rapidly through email, causing severe damage to files and systems. |
8. Rootkits
Rootkits are one of the most insidious types of malware, designed to burrow deep into a system, often operating at the core level to hide their presence. Once installed, they grant cybercriminals elevated privileges, allowing them to bypass security measures and maintain control over an infected device. Rootkits work silently in the background, often without alerting users or security software. Their primary function is to mask the existence of other malicious programs, making detection a near-impossible task. Unlike other types of malware that cause immediate damage, rootkits are stealthy, allowing attackers to harvest sensitive data or control the system remotely.
They are typically installed via vulnerabilities or social engineering tactics, making prevention difficult. To combat rootkits, advanced detection tools and regular system audits are essential. Once infected, the only surefire way to remove a rootkit is often a complete system reinstallation, underscoring the importance of layered security.
| Rootkit Name | Description | Functionality |
| TDL-4 (TDL4) | One of the most sophisticated rootkits, TDL-4 operates by hiding its presence from antivirus software and other system monitoring tools. | Provides remote access to infected systems, manipulates traffic, and can infect the MBR, making it difficult to detect and remove. |
| Stuxnet | A highly advanced rootkit that targeted industrial control systems, particularly in Iran’s nuclear facilities. | Modifies the operation of specific industrial control software, sabotages physical equipment, and spreads via USB drives and networks. |
| Zeus | A rootkit primarily used in banking malware attacks, hiding the presence of malicious processes on infected machines. | Conceals its own malicious activities, allows remote access, and enables the theft of sensitive data, such as banking credentials. |
| Nivdort | A rootkit that is known for its ability to hide malicious processes and files from both users and security programs. | Steals sensitive information, manipulates network traffic, and often serves as a backdoor for additional malware or remote control. |
| R2D2 Rootkit | A lesser-known rootkit designed to infiltrate and hide malware in Windows systems, particularly by masking malicious drivers and executables. | Disguises the presence of its malicious components, prevents detection, and allows attackers to remotely control infected systems. |
| FuRoot | A rootkit that targets Linux systems and operates by modifying kernel functions to hide processes, files, and network connections. | Ensures that attackers can maintain persistent access to infected systems while evading detection by security software. |
| Carbanak | A rootkit used by an advanced cybercriminal group to infiltrate financial institutions, enabling the stealing of millions of dollars. | Enables attackers to gain control of ATM networks, manipulate financial transactions, and cover their tracks by hiding the presence of malware. |
| FinFisher | A rootkit used in highly targeted surveillance operations, often by law enforcement or government agencies. | Provides full remote control over infected systems, captures data, and enables continuous monitoring without detection. |
| ZeroAccess | A rootkit known for infecting large numbers of systems to create a botnet for click fraud and DDoS attacks. | Conceals the presence of its files and processes, makes use of a peer-to-peer network to communicate, and avoids detection by antivirus tools. |
| Rbot | A rootkit that allows attackers to create a botnet and perform malicious actions, often using backdoors to infect multiple systems. | Spreads via IRC, creates a botnet, and facilitates remote control for malicious actions like launching DDoS attacks or stealing data. |
9. Keyloggers
Keyloggers are a nefarious type of malware designed to silently capture every keystroke made on a compromised device. Often hiding in the background, they record sensitive information like passwords, credit card details, and personal messages. Unlike other types of malware, keyloggers are less about immediate disruption and more about long-term data theft. They can be installed through phishing emails, malicious downloads, or even via hardware-based methods. Once activated, keyloggers send their stolen data to cybercriminals, often without the user ever noticing.
The dangers of keyloggers extend beyond personal information theft—they can facilitate identity fraud, financial theft, and corporate espionage. Protecting against keyloggers requires a combination of vigilant security practices, like avoiding suspicious links, using encrypted communications, and employing comprehensive anti-malware solutions that detect unusual activity. Regular updates and strong password management further fortify defenses against these stealthy attackers.
| Keylogger Name | Description | Functionality |
| SpyAgent | A commercial keylogger software used for monitoring employee activity, parents’ monitoring, and catching cheating partners. | Logs keystrokes, records screenshots, and captures clipboard data, allowing users to monitor user behavior on a computer. |
| Revealer Keylogger | A user-friendly keylogger designed to be undetectable and stealthy, intended for personal monitoring and parental control. | Tracks keystrokes, emails, chat messages, and user activity, making it useful for monitoring children or employees in the workplace. |
| Elite Keylogger | A powerful keylogger designed for corporate espionage, allowing attackers to record emails, clipboard data, and web browser activity. | Logs keystrokes, browsing history, screenshots, and can send reports to the attacker through encrypted email. |
| Perfect Keylogger | A keylogger that operates with high stealth and minimal system impact, focusing on privacy and personal security. | Records typed keystrokes, stores passwords, and logs system events without affecting the performance of the computer. |
| Ainsoft Keylogger | A keylogger aimed at capturing login information and browser history, typically used for monitoring workplace activity. | Monitors user behavior, records passwords and sensitive information typed on the keyboard, and tracks clipboard data. |
| HawkEye Keylogger | A keylogger designed for remote monitoring, especially in corporate environments to capture sensitive data and employee behavior. | Records keystrokes, captures screenshots, and stores clipboard data; also allows remote control of infected systems. |
| ReKey | An open-source keylogger tool for ethical hacking and penetration testing, used to monitor user input and behavior. | Tracks keystrokes and user activity, typically used in a controlled environment for testing system vulnerabilities. |
| DarkComet Keylogger | A malicious keylogger used in cyber espionage and surveillance campaigns, particularly in government-targeted attacks. | Records user keystrokes, emails, passwords, and sensitive data; also allows remote control of infected systems and spying activities. |
| RatsKeylogger | A keylogger variant known for capturing keyboard input and sending data back to a remote server using encrypted channels. | Used in sophisticated cyberattacks, especially in malware campaigns targeting large organizations. |
| Spyware Terminator Keylogger | A keylogger component embedded in broader anti-malware solutions, designed to provide monitoring and tracking without compromising user security. | Tracks user behavior, keystrokes, clipboard data, and system activity without adversely affecting system performance. |
10. Bots/Botnets
Bots are a particularly dangerous type of malware that take control of an infected device, turning it into a zombie. Once infected, a bot communicates with a central command server, following orders without the user’s knowledge. When multiple bots are linked together, they form a botnet, a network of compromised devices working in unison. Botnets are used for a variety of malicious activities, including launching Distributed Denial-of-Service (DDoS) attacks, spreading spam, or stealing sensitive data.
Unlike other types of malware, bots often remain hidden, allowing them to remain undetected for extended periods. Their ability to scale and perform coordinated attacks makes them especially formidable. The rise of IoT devices has only increased the scope of botnet attacks, with everyday appliances becoming unwitting accomplices. Defending against bots and botnets requires advanced threat detection systems, frequent software updates, and vigilant monitoring of unusual network traffic.
| Bot/Botnet Name | Description | Functionality |
| Mirai | A notorious botnet that primarily uses IoT devices, such as cameras and routers, to create a massive network for DDoS attacks. | Exploits weak passwords to compromise IoT devices and launch large-scale DDoS attacks, taking down websites and online services. |
| Emotet | Initially a banking Trojan, Emotet evolved into a powerful botnet used for distributing malware and stealing sensitive information. | Spreads via phishing emails and malicious attachments, enabling the installation of other malware and forming a botnet for large-scale attacks. |
| Zeus | A widely known botnet used to steal sensitive information, particularly banking credentials, through keylogging and form grabbing. | Operates by infecting systems, stealing financial data, and spreading to other systems, often creating a botnet for further exploitation. |
| Conficker | A botnet that became one of the largest and most dangerous in history, infecting millions of computers worldwide. | Exploits vulnerabilities in Windows systems to create a botnet, steals sensitive data, and can download additional malicious software. |
| Srizbi | A botnet known for its massive spam email campaigns, often used to deliver additional malware like ransomware and phishing links. | Infects systems through email attachments or infected websites, creating a botnet that sends out spam, steals credentials, and spreads malware. |
| Kelihos | A botnet responsible for sending spam emails and distributing malware, particularly targeting financial data and login credentials. | Uses compromised computers to launch spam campaigns, steal personal information, and distribute ransomware, often forming large botnets. |
| Andromeda | A highly flexible botnet used to distribute a wide variety of malware, including ransomware, Trojans, and information-stealing payloads. | Spreads through phishing emails, malicious downloads, and infected websites, allowing hackers to control infected systems and install malware. |
| ZeroAccess | A powerful botnet designed for financial fraud and click fraud, infecting computers and creating a peer-to-peer network for malicious purposes. | Uses infected machines to participate in click fraud, redirect web traffic, and launch DDoS attacks, while maintaining persistence and evasion. |
| Nitol | A botnet primarily used for launching DDoS attacks and distributing other types of malware, including rootkits and keyloggers. | Leverages compromised systems to distribute spam, launch DDoS attacks, and install other types of malware for cybercriminal operations. |
| Fbot | A lesser-known botnet that primarily spreads through phishing emails and can control a large network of infected machines for various malicious activities. | Infiltrates devices via phishing, creates a botnet, and is used for cyberattacks, such as credential theft, spamming, and DDoS operations. |
11. Mobile Malware
Mobile malware is a rapidly growing threat, targeting smartphones and tablets—devices that are central to modern life. As one of the most prevalent types of malware, mobile malware comes in various forms, including spyware, adware, and even ransomware. These malicious apps often masquerade as legitimate software, tricking users into downloading them from third-party app stores or malicious links. Once installed, mobile malware can steal personal data, track location, or hijack a device for use in larger botnets.
Unlike traditional desktop malware, mobile malware exploits the always-connected nature of smartphones, making it harder to detect and defend against. To protect against this digital threat, users must avoid downloading apps from untrusted sources, regularly update software, and use security apps designed to spot suspicious activity. Given the rise in mobile device dependency, the consequences of a mobile malware infection can be far-reaching, from privacy breaches to financial loss.
| Mobile Malware Name | Description | Functionality |
| Joker | A notorious mobile malware that targets Android devices, often hidden in seemingly benign apps available on the Google Play Store. | Steals SMS messages, contacts, and device information; subscribes victims to premium services without their consent. |
| Cerberus | A sophisticated Android mobile malware that is primarily used for stealing banking information and bypassing multi-factor authentication (MFA). | Exploits accessibility services to capture user input, steal credentials, and gain access to bank accounts or sensitive applications. |
| XcodeGhost | A highly impactful mobile malware targeting iOS devices, spread through a compromised version of Apple’s Xcode development tool. | Injects malicious code into apps, stealing sensitive user data like Apple ID credentials, and causing affected apps to act maliciously. |
| Flubot | A rapidly spreading mobile malware affecting Android devices, often distributed through SMS phishing campaigns. | Steals banking credentials, logs keystrokes, and spreads via malicious links sent through text messages. |
| BankBot | A mobile malware targeting Android devices, specifically designed to steal banking credentials from a variety of banking apps. | Mimics legitimate banking apps, records user input, and steals banking login information through phishing-like behavior. |
| AdClicker | A mobile malware that primarily targets Android devices, usually bundled with adware that serves intrusive advertisements to the user. | Engages in ad fraud by clicking on ads automatically, generating revenue for cybercriminals, and compromising device performance. |
| Trojan-SMS | A type of mobile malware that targets Android devices, spreading through SMS messages and infected apps. | Sends premium-rate SMS messages, steals information from the victim’s device, and often subscribes users to expensive services unknowingly. |
| Agent Smith | A mobile malware that primarily affects Android devices by exploiting vulnerabilities in older versions of the OS. | Replaces legitimate apps with malicious versions, collects user data, and installs additional malware without the user’s knowledge. |
| Ghost Push | A mobile malware that primarily targets Android devices, known for being difficult to remove and capable of installing other malicious software. | Forces unwanted apps to be installed on the device, drains battery life, and often makes the device vulnerable to further attacks. |
| Mazar | A mobile malware that specifically targets Android users in the Middle East and Central Asia, often distributed via malicious apps on third-party stores. | Steals sensitive information like banking credentials, user data, and bypasses security measures to avoid detection by users or antivirus tools. |
12. Wiper Malware
Wiper malware is one of the most destructive types of malware, designed to erase data irretrievably from compromised systems. Unlike ransomware, which holds data hostage, wiper malware aims to completely wipe out critical information, rendering it useless. Once activated, it overwrites files and system configurations, leaving no trace of the original data behind. This malicious software is often used in cyberattacks targeting organizations or nations, designed to cripple infrastructure or erase sensitive intelligence.
Wiper malware can spread via phishing emails, compromised software, or security vulnerabilities. Its effects can be catastrophic, resulting in massive data loss, operational downtime, and financial devastation. To mitigate the risk, organizations should implement rigorous backup protocols, regularly test recovery systems, and maintain up-to-date security measures to detect and block such threats. The purpose of wiper malware is not profit, but sheer destruction, making it one of the most perilous types of malware in existence.
| Wiper Malware Name | Description | Functionality |
| Shamoon | A notorious wiper malware that targets systems in the Middle East, particularly those in the energy sector. | Deletes data and overwrites system files, rendering infected computers inoperable and causing massive data loss in critical industries. |
| StoneDrill | A sophisticated wiper malware believed to be linked to Iranian cyber activities, designed to wipe data from infected systems and cause extensive disruption. | Destroys data, damages files, and manipulates the operating system to erase all traces of the malware. |
| KillDisk | A wiper malware used in cyberattacks, specifically to destroy data on critical systems and disrupt business operations, often in state-sponsored cyber espionage. | Deletes and overwrites data, renders hard drives unusable, and creates substantial financial and operational damage. |
| NotPetya | A wiper malware initially disguised as ransomware but ultimately used to cause destruction, primarily targeting Ukrainian businesses in 2017. | Encrypts and wipes data, rendering systems completely inaccessible and destroying business-critical information. |
| Crobat | A wiper malware designed to wipe data from infected machines, typically used in targeted attacks against specific organizations or governments. | Erases files and partitions, making it nearly impossible to recover the data, disrupting operations across various industries. |
| Bad Rabbit | A wiper malware that spreads via fake software updates, primarily affecting targets in Eastern Europe. | Encrypts and deletes files, disrupting operations and leading to significant data loss in infected networks. |
| Fanny | A wiper malware used to target specific organizations in the Middle East, aimed at damaging key data and disrupting operations. | Destroys data on infected systems and leaves the machines inoperable, often part of a wider campaign of cyber sabotage. |
| RIPPER | A wiper malware used in cyberattacks designed to wipe data from financial institutions and critical infrastructure, rendering them inoperable. | Overwrites files and erases data from the infected system, leaving no trace and causing severe disruptions in business operations. |
| Wiper | A simple yet effective wiper malware that focuses on deleting files and erasing system data, often employed in targeted attacks against individual users. | Deletes files, corrupts data, and leaves systems unusable, typically causing significant data loss in personal and professional environments. |
| ZeroCleare | A wiper malware attributed to attacks on the energy sector in the Middle East, aimed at creating widespread operational disruptions. | Corrupts and deletes data from critical infrastructure, impacting industrial control systems and causing severe operational downtime. |
The ever-evolving landscape of types of malware demands constant vigilance—what protects you today might not be enough tomorrow.
Conclusion
Understanding the various types of malware is crucial in today’s digital landscape. From the silent invasion of keyloggers to the devastating destruction caused by wiper malware, these threats are more sophisticated than ever. Whether targeting individuals or large organizations, malware can cause irreversible damage if left unchecked. Prevention, vigilance, and a strong security framework are key to mitigating the risks. Regular updates, comprehensive antivirus solutions, and user education are vital components in defending against these malicious intruders. As cyber threats evolve, staying informed about the latest types of malware will empower users to protect their data and systems from harm.
Knowledge of the types of malware is not just power, it’s protection; the more you know, the safer your data becomes.
FAQ: The 12 Most Common Types of Malware
- What are the different types of malware?
- Types of malware include ransomware, viruses, Trojans, spyware, worms, rootkits, and more. Each serves a unique purpose, from stealing data to causing system damage.
- How do I protect myself from the various types of malware?
- To defend against types of malware, use antivirus software, update your operating system regularly, avoid suspicious links, and practice safe browsing habits.
- What is the most dangerous type of malware?
- Wiper malware is often considered one of the most destructive types of malware, as it erases data permanently, causing irreparable damage to systems and information.
- Can malware be spread through email attachments?
- Yes, many types of malware, including Trojans and worms, can be spread through malicious email attachments or links, which users unknowingly click on.
- Are mobile devices vulnerable to types of malware?
- Yes, mobile devices are susceptible to types of malware like mobile ransomware, spyware, and adware. Always download apps from trusted sources and keep your device updated.
- How can I detect types of malware on my system?
- Regularly scan your system with reputable antivirus tools, monitor unusual behaviors, and look out for system slowdowns, which are signs that types of malware may be present.
- What is the difference between a virus and a worm?
- While both are types of malware, a virus requires a host file to replicate, while a worm spreads independently across networks, often without user intervention.



Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.